Server Man
Well-Known Member
- May 17, 2015
~ Irfan Rabbani | Senior Support Escalation Engineer
 This article is the second in my series of posts on how to monitor System Center 2012 R2 Operations Manager clients that are not members of your Active Directory domain. The series is broken out into three parts:
This article is the second in my series of posts on how to monitor System Center 2012 R2 Operations Manager clients that are not members of your Active Directory domain. The series is broken out into three parts:
Part 1: Installing the Microsoft Certificate Authority Server for Operations Manager certificate based authentication
Part 2: Installing certificates and final configuration
Part 3: Installing and configuring a gateway
Here in part 2 we’ll be installing the Operations Manager certificates, configuring OpsMgr and then setting up monitoring for a workgroup client. Note that this scenario describes how to install an untrusted agent on a Windows Server 2008 R2 X64 computer that resides in an untrusted domain when no gateway is used. Information on the use of gateway servers will be covered in part 3.
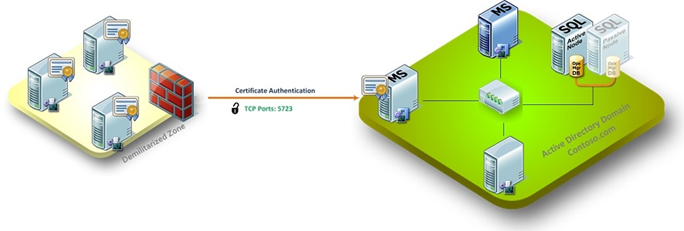
Step 1. Open TCP port 5723
You will need to take the necessary steps to open port 5723 from the client to the management server in your environment. What those steps may be will vary depending on your network configuration. For further help with this you may need to contact your local network specialist.
To verify connectivity, go to the client and open the command prompt, then in the command prompt run telnet x.x.x.x 5732 (where x.x.x.x is the IP address of the management server). If everything is working, continue to the next step. If not, be sure that the firewall is open and is passing traffic on port 5723.
Step 2. Install the Root CA certificate on the client
1. From the client, start Internet Explorer.
2. Go to the certificate server website (e.g. http://MyServer/Certsrv)
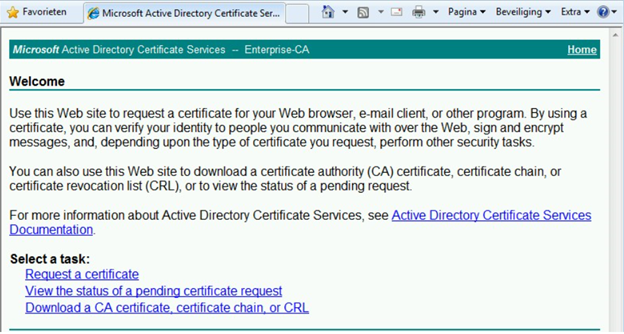
3. Click on Download CA certificate, certificate chain, or CRL.
4. Click Download CA Certificate chain and save it.
5. Once the certificate is downloaded, open MMC and connect to Local Computer, then load the certificates snap-in (Local Computer).
6. Go to Trusted Root Certification Authorities and right-click, then select all tasks, import and import the Root CA.
Step 3. Install the computer certificate on the client
1. From the client, start Internet Explorer.
2. Go to the certificate server website:
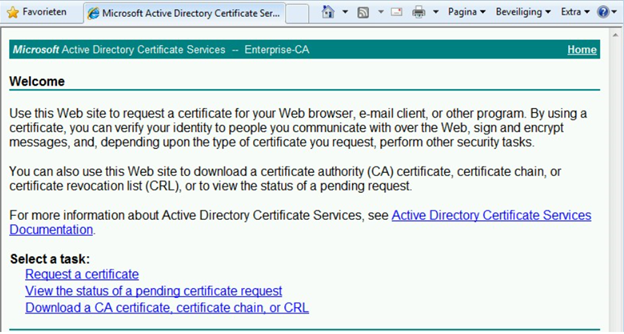
3. Click on Request a certificate, choose Advanced certificate request then click Create and submit a request to this CA.
4. Choose the OpsMgr Certificate template, in the name tab choose the FQDN of the machine and fill in the same name for the friendly name.
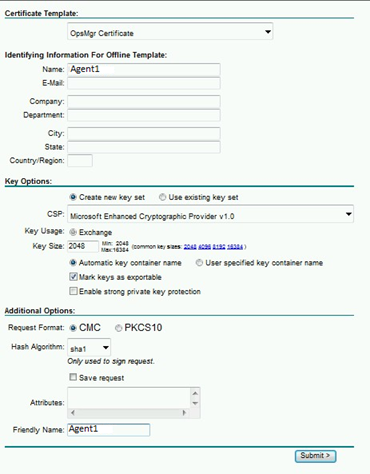
5. Click Finish and install the certificate. Once installed, the certificate is stored by default in the personal certificate store, however the OpsMgr certificate need to be in the computer store so our next step is to move it.
6. To move the certificate, click Start, click Run, and run MMC.
7. On the File menu, click Add/Remove Snap-in then click Add and click Certificates, and then click Add, select Personal Store and Computer account, then click Finish.
8. Export the certificate from the personal store and import it to the local computer store (no drag and drop here).
9. Remove the certificate from the local user store.
10. Make sure that both the client and the server are reachable via hostname (just ping). If it’s not working add the computers in DNS or in the Host file (C:\Windows\System32\Drivers\ETC\Host).
Step 4. Install the Root CA Certificate on the Management Server
1. From the client, start Internet Explorer.
2. Go to the certificate server website:
3. Click on Download CA certificate, certificate chain, or CRL.
4. Click Download CA Certificate chain and save it.
5. Once the certificate is downloaded, open MMC and connect to Local Computer, then load the certificates snap-in (Local Computer).
6. Go to Trusted Root Certification Authorities, right-click, select all tasks, import and import the Root CA.
Step 5. Install the Computer Certificate on the Management Server
1. From the client, start Internet Explorer.
2. Go to the certificate server website:
3. Click on Request a certificate, choose Advanced certificate request, then click Create and submit a request to this CA.
4. Choose the OpsMgr Certificate template, then in the name tab choose the FQDN name of the machine and fill in the same name for the friendly name.
5. Click Finish and install the certificate. The certificate will now be stored in the personal certificate store, however the OpsMgr certificate actually needs to be in the computer store so we now must move it.
6. To move the certificate, click Start, click Run, and run MMC.
7. On the File menu, click Add/Remove Snap-in then click Add and click Certificates, and then click Add, select Personal Store and Computer account, then click Finish.
8. Export the certificate from the personal store and import it to the local computer store (no drag and drop here).
9. Remove the certificate from the local user store.
10. Make sure that both the client and the server are reachable via hostname (just ping). If it’s not working add the computers in DNS or in the Host file (C:\Windows\System32\Drivers\ETC\Host).
Step 6. Configure Operations Manager for Manually Installed Clients
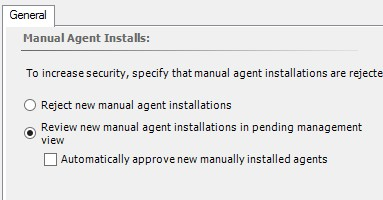
1. First we need to make sure new agents are not rejected. To do this, go to the Operations Manager console –> Administration –> Settings –> Security and select Review new manual agent installations in pending management view.
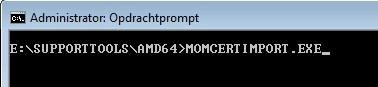
2. Now we need to import the certificate on the management server. Go to the support tools folder and run MOMCertimport.exe.
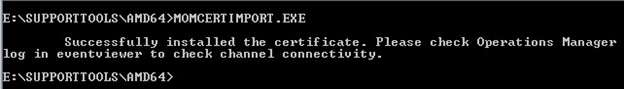
3. Select the imported certificate and click OK. Make sure this completes successfully.
Step 7. Manually Install Agents on Clients and Run MOMCertImport
1. From the client, go to the OpsMgr agent installation folder. By default this is \\DISK\Program Files\System Center 2012\Operations Manager\Server\AgentManagement\ in the AMD64 or i386 folder. If not available you can simply copy this to the client. Run Momagent.MSI to install the agent.
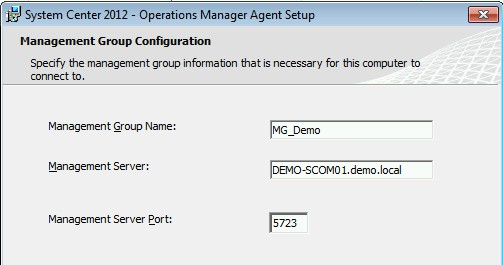
2. Fill in the proper settings for the monitoring group (I used the settings below).
3. I prefer using the Local System account. Choose Next and Install.
4. If necessary, update the agent with the required updates.
5. Copy the Support Tools directory from the OpsMgr installation media to the client.
6. On the client machine, open a Command Prompt (Run As Administrator)
7. Go to the copied support tools directory and run MOMCertimport.exe:
8. Select the imported certificate and click OK.
9. Make sure the import was successful:
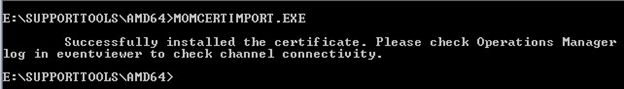
Step 8. Approve Agents in the Operations Manager Console
NOTE Be aware that it can take a while before the client shows up in the console.
1. Open the Operations Manager console and go to Administration –> Pending Management.
2. Right-click the client and select Approve.
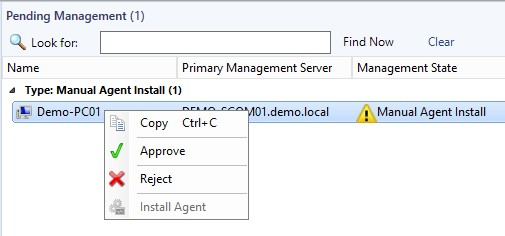
That’s it! Your client is now monitored.
Troubleshooting
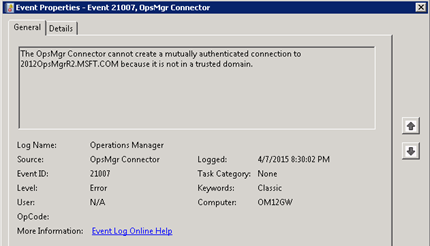
A gateway server or client without the proper certificate that tries to communicate with a management server using Kerberos from a non-trusted realm will log the following:
Log Name: Operations Manager
Source: OpsMgr Connector
Event ID: 21007
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: SERVER
Description:
The OpsMgr Connector cannot create a mutually authenticated connection to SERVER.DOMAIN.COM because it is not in a trusted domain.
=====
A gateway server or client agent using a certificate to communicate with a management server will log the following if the root certificate is not installed:
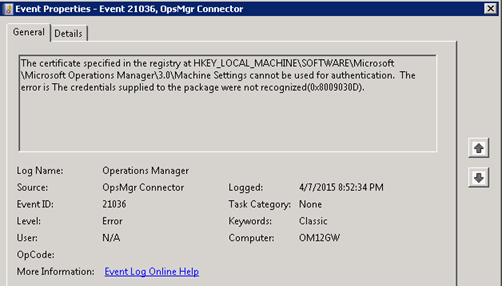
Log Name: Operations Manager
Source: OpsMgr Connector
Event ID: 21036
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: OM12GW
Description:
The certificate specified in the registry at HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft Operations Manager\3.0\Machine Settings cannot be used for authentication. The error is The credentials supplied to the package were not recognized(0x8009030D).
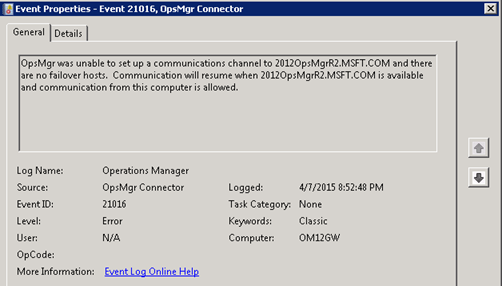
Log Name: Operations Manager
Source: OpsMgr Connector
Event ID: 21016
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: OM12GW
Description:
OpsMgr was unable to set up a communications channel to SERVER.DOMAIN.COM and there are no failover hosts. Communication will resume when SERVER.DOMAIN.COM is available and communication from this computer is allowed.
=====
If the computer certificate does not have a SubjectName that matches the full computer name then you will see the following:
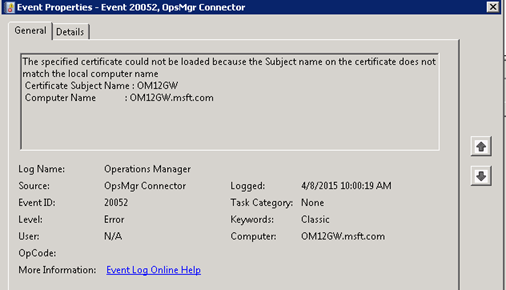
=====
If the Extensions/Enhanced Key usage is not met, you will see the following event indicating that the certificate does not have Server Authentication/Client Authentication enabled.
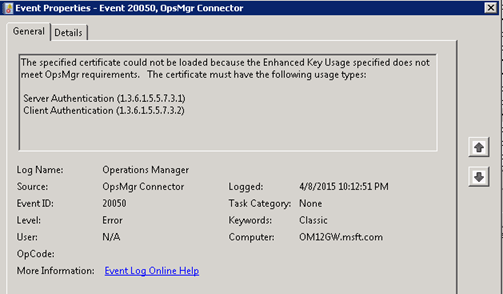
Log Name: Operations Manager
Source: OpsMgr Connector
Event ID: 20050
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: OM12GW.msft.com
Description:
The specified certificate could not be loaded because the Enhanced Key Usage specified does not meet OpsMgr requirements. The certificate must have the following usage types:
Server Authentication (1.3.6.1.5.5.7.3.1)
Client Authentication (1.3.6.1.5.5.7.3.2)
=====
If the Root CA is different on the gateway server or client versus the management server, meaning the gateway or client got its certificate from a different root chain PKI than the management server, you will see the following.
On the gateway or client:
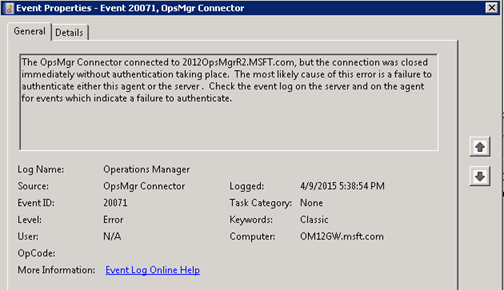
Log Name: Operations Manager
Source: OpsMgr Connector
Date: 4/9/2015 5:38:54 PM
Event ID: 20071
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: OM12GW.msft.com
Description:
The OpsMgr Connector connected to 2012OpsMgrR2.MSFT.com, but the connection was closed immediately without authentication taking place. The most likely cause of this error is a failure to authenticate either this agent or the server . Check the event log on the server and on the agent for events which indicate a failure to authenticate.
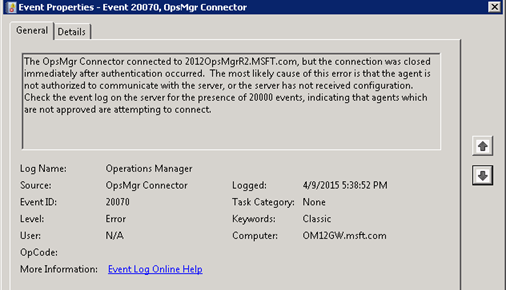
Log Name: Operations Manager
Source: OpsMgr Connector
Date: 4/9/2015 5:38:52 PM
Event ID: 20070
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: OM12GW.msft.com
Description:
The OpsMgr Connector connected to 2012OpsMgrR2.MSFT.com, but the connection was closed immediately after authentication occurred. The most likely cause of this error is that the agent is not authorized to communicate with the server, or the server has not received configuration. Check the event log on the server for the presence of 20000 events, indicating that agents which are not approved are attempting to connect.
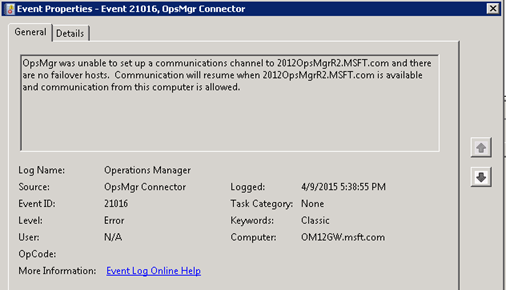
Log Name: Operations Manager
Source: OpsMgr Connector
Date: 4/9/2015 5:38:55 PM
Event ID: 21016
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: OM12GW.msft.com
Description:
OpsMgr was unable to set up a communications channel to 2012OpsMgrR2.MSFT.com and there are no failover hosts. Communication will resume when 2012OpsMgrR2.MSFT.com is available and communication from this computer is allowed.
On the management server:
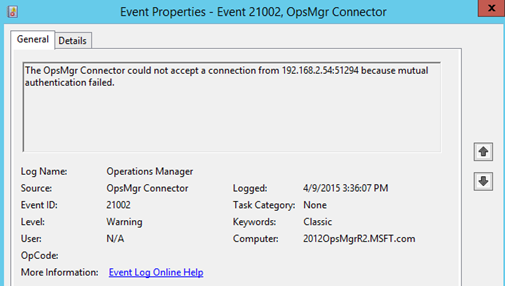
Log Name: Operations Manager
Source: OpsMgr Connector
Date: 4/9/2015 3:36:07 PM
Event ID: 21002
Task Category: None
Level: Warning
Keywords: Classic
User: N/A
Computer: 2012OpsMgrR2.MSFT.com
Description:
The OpsMgr Connector could not accept a connection from 192.168.2.54:51294 because mutual authentication failed.
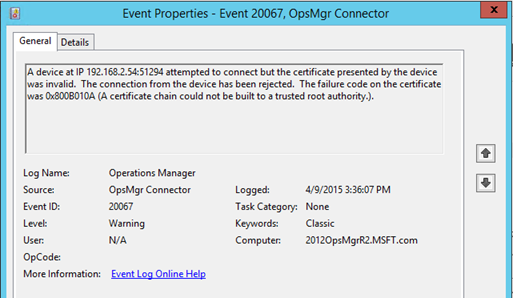
Log Name: Operations Manager
Source: OpsMgr Connector
Date: 4/9/2015 3:36:07 PM
Event ID: 20067
Task Category: None
Level: Warning
Keywords: Classic
User: N/A
Computer: 2012OpsMgrR2.MSFT.com
Description:
A device at IP 192.168.2.54:51294 attempted to connect but the certificate presented by the device was invalid. The connection from the device has been rejected. The failure code on the certificate was 0x800B010A (A certificate chain could not be built to a trusted root authority.).
Additional Information
How to Obtain a Certificate Using Windows Server 2008 Enterprise CA in Ops Manager 2007: http://technet.microsoft.com/en-us/library/dd362553.aspx
How to Obtain a Certificate Using Windows Server 2008 Stand-Alone CA in Ops Manager 2007: http://technet.microsoft.com/en-us/library/dd362655.aspx
How to Obtain a Certificate Using Windows Server 2003 Enterprise CA in Ops Manager 2007: http://technet.microsoft.com/en-us/library/bb735413.aspx
How to Obtain a Certificate Using Windows Server 2003 Stand-Alone CA in Ops Manager 2007: http://technet.microsoft.com/en-us/library/bb735417.aspx
Authentication and Data Encryption for Windows Computers: https://technet.microsoft.com/en-us/library/hh212810.aspx
That should take care of getting our certificates installed and Operations Manager configured for these untrusted clients. In my next installment I’ll talk about installing a gateway for use in larger environments.
Irfan Rabbani | Senior Support Escalation Engineer | Microsoft GBS Management and Security Division
Get the latest System Center news on Facebook and Twitter:


System Center All Up: http://blogs.technet.com/b/systemcenter/
Configuration Manager Support Team blog: http://blogs.technet.com/configurationmgr/
Data Protection Manager Team blog: http://blogs.technet.com/dpm/
Orchestrator Support Team blog: http://blogs.technet.com/b/orchestrator/
Operations Manager Team blog: http://blogs.technet.com/momteam/
Service Manager Team blog: http://blogs.technet.com/b/servicemanager
Virtual Machine Manager Team blog: http://blogs.technet.com/scvmm
Microsoft Intune: http://blogs.technet.com/b/microsoftintune/
WSUS Support Team blog: http://blogs.technet.com/sus/
The RMS blog: http://blogs.technet.com/b/rms/
App-V Team blog: http://blogs.technet.com/appv/
MED-V Team blog: http://blogs.technet.com/medv/
Server App-V Team blog: http://blogs.technet.com/b/serverappv
The Surface Team blog: http://blogs.technet.com/b/surface/
The Application Proxy blog: http://blogs.technet.com/b/applicationproxyblog/
The Forefront Endpoint Protection blog : http://blogs.technet.com/b/clientsecurity/
The Forefront Identity Manager blog : http://blogs.msdn.com/b/ms-identity-support/
The Forefront TMG blog: http://blogs.technet.com/b/isablog/
The Forefront UAG blog: http://blogs.technet.com/b/edgeaccessblog/
OpsMgr 2012 R2

Continue reading...

Part 1: Installing the Microsoft Certificate Authority Server for Operations Manager certificate based authentication
Part 2: Installing certificates and final configuration
Part 3: Installing and configuring a gateway
Here in part 2 we’ll be installing the Operations Manager certificates, configuring OpsMgr and then setting up monitoring for a workgroup client. Note that this scenario describes how to install an untrusted agent on a Windows Server 2008 R2 X64 computer that resides in an untrusted domain when no gateway is used. Information on the use of gateway servers will be covered in part 3.

Step 1. Open TCP port 5723
You will need to take the necessary steps to open port 5723 from the client to the management server in your environment. What those steps may be will vary depending on your network configuration. For further help with this you may need to contact your local network specialist.
To verify connectivity, go to the client and open the command prompt, then in the command prompt run telnet x.x.x.x 5732 (where x.x.x.x is the IP address of the management server). If everything is working, continue to the next step. If not, be sure that the firewall is open and is passing traffic on port 5723.
Step 2. Install the Root CA certificate on the client
1. From the client, start Internet Explorer.
2. Go to the certificate server website (e.g. http://MyServer/Certsrv)

3. Click on Download CA certificate, certificate chain, or CRL.
4. Click Download CA Certificate chain and save it.
5. Once the certificate is downloaded, open MMC and connect to Local Computer, then load the certificates snap-in (Local Computer).
6. Go to Trusted Root Certification Authorities and right-click, then select all tasks, import and import the Root CA.

Step 3. Install the computer certificate on the client
1. From the client, start Internet Explorer.
2. Go to the certificate server website:

3. Click on Request a certificate, choose Advanced certificate request then click Create and submit a request to this CA.
4. Choose the OpsMgr Certificate template, in the name tab choose the FQDN of the machine and fill in the same name for the friendly name.

5. Click Finish and install the certificate. Once installed, the certificate is stored by default in the personal certificate store, however the OpsMgr certificate need to be in the computer store so our next step is to move it.
6. To move the certificate, click Start, click Run, and run MMC.
7. On the File menu, click Add/Remove Snap-in then click Add and click Certificates, and then click Add, select Personal Store and Computer account, then click Finish.
8. Export the certificate from the personal store and import it to the local computer store (no drag and drop here).
9. Remove the certificate from the local user store.
10. Make sure that both the client and the server are reachable via hostname (just ping). If it’s not working add the computers in DNS or in the Host file (C:\Windows\System32\Drivers\ETC\Host).
Step 4. Install the Root CA Certificate on the Management Server
1. From the client, start Internet Explorer.
2. Go to the certificate server website:

3. Click on Download CA certificate, certificate chain, or CRL.
4. Click Download CA Certificate chain and save it.
5. Once the certificate is downloaded, open MMC and connect to Local Computer, then load the certificates snap-in (Local Computer).
6. Go to Trusted Root Certification Authorities, right-click, select all tasks, import and import the Root CA.

Step 5. Install the Computer Certificate on the Management Server
1. From the client, start Internet Explorer.
2. Go to the certificate server website:

3. Click on Request a certificate, choose Advanced certificate request, then click Create and submit a request to this CA.
4. Choose the OpsMgr Certificate template, then in the name tab choose the FQDN name of the machine and fill in the same name for the friendly name.
5. Click Finish and install the certificate. The certificate will now be stored in the personal certificate store, however the OpsMgr certificate actually needs to be in the computer store so we now must move it.
6. To move the certificate, click Start, click Run, and run MMC.
7. On the File menu, click Add/Remove Snap-in then click Add and click Certificates, and then click Add, select Personal Store and Computer account, then click Finish.
8. Export the certificate from the personal store and import it to the local computer store (no drag and drop here).
9. Remove the certificate from the local user store.
10. Make sure that both the client and the server are reachable via hostname (just ping). If it’s not working add the computers in DNS or in the Host file (C:\Windows\System32\Drivers\ETC\Host).
Step 6. Configure Operations Manager for Manually Installed Clients
1. First we need to make sure new agents are not rejected. To do this, go to the Operations Manager console –> Administration –> Settings –> Security and select Review new manual agent installations in pending management view.

2. Now we need to import the certificate on the management server. Go to the support tools folder and run MOMCertimport.exe.

3. Select the imported certificate and click OK. Make sure this completes successfully.

Step 7. Manually Install Agents on Clients and Run MOMCertImport
1. From the client, go to the OpsMgr agent installation folder. By default this is \\DISK\Program Files\System Center 2012\Operations Manager\Server\AgentManagement\ in the AMD64 or i386 folder. If not available you can simply copy this to the client. Run Momagent.MSI to install the agent.
2. Fill in the proper settings for the monitoring group (I used the settings below).

3. I prefer using the Local System account. Choose Next and Install.
4. If necessary, update the agent with the required updates.
5. Copy the Support Tools directory from the OpsMgr installation media to the client.
6. On the client machine, open a Command Prompt (Run As Administrator)
7. Go to the copied support tools directory and run MOMCertimport.exe:

8. Select the imported certificate and click OK.
9. Make sure the import was successful:

Step 8. Approve Agents in the Operations Manager Console
NOTE Be aware that it can take a while before the client shows up in the console.
1. Open the Operations Manager console and go to Administration –> Pending Management.
2. Right-click the client and select Approve.

That’s it! Your client is now monitored.
Troubleshooting
A gateway server or client without the proper certificate that tries to communicate with a management server using Kerberos from a non-trusted realm will log the following:

Log Name: Operations Manager
Source: OpsMgr Connector
Event ID: 21007
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: SERVER
Description:
The OpsMgr Connector cannot create a mutually authenticated connection to SERVER.DOMAIN.COM because it is not in a trusted domain.
=====
A gateway server or client agent using a certificate to communicate with a management server will log the following if the root certificate is not installed:

Log Name: Operations Manager
Source: OpsMgr Connector
Event ID: 21036
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: OM12GW
Description:
The certificate specified in the registry at HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Microsoft Operations Manager\3.0\Machine Settings cannot be used for authentication. The error is The credentials supplied to the package were not recognized(0x8009030D).

Log Name: Operations Manager
Source: OpsMgr Connector
Event ID: 21016
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: OM12GW
Description:
OpsMgr was unable to set up a communications channel to SERVER.DOMAIN.COM and there are no failover hosts. Communication will resume when SERVER.DOMAIN.COM is available and communication from this computer is allowed.
=====
If the computer certificate does not have a SubjectName that matches the full computer name then you will see the following:

=====
If the Extensions/Enhanced Key usage is not met, you will see the following event indicating that the certificate does not have Server Authentication/Client Authentication enabled.

Log Name: Operations Manager
Source: OpsMgr Connector
Event ID: 20050
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: OM12GW.msft.com
Description:
The specified certificate could not be loaded because the Enhanced Key Usage specified does not meet OpsMgr requirements. The certificate must have the following usage types:
Server Authentication (1.3.6.1.5.5.7.3.1)
Client Authentication (1.3.6.1.5.5.7.3.2)
=====
If the Root CA is different on the gateway server or client versus the management server, meaning the gateway or client got its certificate from a different root chain PKI than the management server, you will see the following.
On the gateway or client:

Log Name: Operations Manager
Source: OpsMgr Connector
Date: 4/9/2015 5:38:54 PM
Event ID: 20071
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: OM12GW.msft.com
Description:
The OpsMgr Connector connected to 2012OpsMgrR2.MSFT.com, but the connection was closed immediately without authentication taking place. The most likely cause of this error is a failure to authenticate either this agent or the server . Check the event log on the server and on the agent for events which indicate a failure to authenticate.

Log Name: Operations Manager
Source: OpsMgr Connector
Date: 4/9/2015 5:38:52 PM
Event ID: 20070
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: OM12GW.msft.com
Description:
The OpsMgr Connector connected to 2012OpsMgrR2.MSFT.com, but the connection was closed immediately after authentication occurred. The most likely cause of this error is that the agent is not authorized to communicate with the server, or the server has not received configuration. Check the event log on the server for the presence of 20000 events, indicating that agents which are not approved are attempting to connect.

Log Name: Operations Manager
Source: OpsMgr Connector
Date: 4/9/2015 5:38:55 PM
Event ID: 21016
Task Category: None
Level: Error
Keywords: Classic
User: N/A
Computer: OM12GW.msft.com
Description:
OpsMgr was unable to set up a communications channel to 2012OpsMgrR2.MSFT.com and there are no failover hosts. Communication will resume when 2012OpsMgrR2.MSFT.com is available and communication from this computer is allowed.
On the management server:

Log Name: Operations Manager
Source: OpsMgr Connector
Date: 4/9/2015 3:36:07 PM
Event ID: 21002
Task Category: None
Level: Warning
Keywords: Classic
User: N/A
Computer: 2012OpsMgrR2.MSFT.com
Description:
The OpsMgr Connector could not accept a connection from 192.168.2.54:51294 because mutual authentication failed.

Log Name: Operations Manager
Source: OpsMgr Connector
Date: 4/9/2015 3:36:07 PM
Event ID: 20067
Task Category: None
Level: Warning
Keywords: Classic
User: N/A
Computer: 2012OpsMgrR2.MSFT.com
Description:
A device at IP 192.168.2.54:51294 attempted to connect but the certificate presented by the device was invalid. The connection from the device has been rejected. The failure code on the certificate was 0x800B010A (A certificate chain could not be built to a trusted root authority.).
Additional Information
How to Obtain a Certificate Using Windows Server 2008 Enterprise CA in Ops Manager 2007: http://technet.microsoft.com/en-us/library/dd362553.aspx
How to Obtain a Certificate Using Windows Server 2008 Stand-Alone CA in Ops Manager 2007: http://technet.microsoft.com/en-us/library/dd362655.aspx
How to Obtain a Certificate Using Windows Server 2003 Enterprise CA in Ops Manager 2007: http://technet.microsoft.com/en-us/library/bb735413.aspx
How to Obtain a Certificate Using Windows Server 2003 Stand-Alone CA in Ops Manager 2007: http://technet.microsoft.com/en-us/library/bb735417.aspx
Authentication and Data Encryption for Windows Computers: https://technet.microsoft.com/en-us/library/hh212810.aspx
That should take care of getting our certificates installed and Operations Manager configured for these untrusted clients. In my next installment I’ll talk about installing a gateway for use in larger environments.
Irfan Rabbani | Senior Support Escalation Engineer | Microsoft GBS Management and Security Division
Get the latest System Center news on Facebook and Twitter:


System Center All Up: http://blogs.technet.com/b/systemcenter/
Configuration Manager Support Team blog: http://blogs.technet.com/configurationmgr/
Data Protection Manager Team blog: http://blogs.technet.com/dpm/
Orchestrator Support Team blog: http://blogs.technet.com/b/orchestrator/
Operations Manager Team blog: http://blogs.technet.com/momteam/
Service Manager Team blog: http://blogs.technet.com/b/servicemanager
Virtual Machine Manager Team blog: http://blogs.technet.com/scvmm
Microsoft Intune: http://blogs.technet.com/b/microsoftintune/
WSUS Support Team blog: http://blogs.technet.com/sus/
The RMS blog: http://blogs.technet.com/b/rms/
App-V Team blog: http://blogs.technet.com/appv/
MED-V Team blog: http://blogs.technet.com/medv/
Server App-V Team blog: http://blogs.technet.com/b/serverappv
The Surface Team blog: http://blogs.technet.com/b/surface/
The Application Proxy blog: http://blogs.technet.com/b/applicationproxyblog/
The Forefront Endpoint Protection blog : http://blogs.technet.com/b/clientsecurity/
The Forefront Identity Manager blog : http://blogs.msdn.com/b/ms-identity-support/
The Forefront TMG blog: http://blogs.technet.com/b/isablog/
The Forefront UAG blog: http://blogs.technet.com/b/edgeaccessblog/
OpsMgr 2012 R2

Continue reading...