Server Man
Well-Known Member
- May 17, 2015

- Windows 10

- Chrome 67.0.3396.87
Howdy folks,
I’m here to share with you the next part in our Eight Essentials for Hybrid Identity blog series, based on what we’ve learned from working with tens of thousands of organizations on this hybrid journey. When setting up single sign-on for your employees and partners to all their SaaS applications and on-premises apps and resources, the first thing we want to do is establish identities in the cloud.
With identities as your control plane, authentication is the foundation for cloud access. Choosing the right authentication method is a crucial decision, but also one that’s different for every organization and might change over time.
To help walk you through this decision, I’ve invited Swaroop, the PM on my team working on these hybrid authentication technologies, to share his insight.
Best Regards,
Alex Simons (Twitter:@Alex_A_Simons)
Director of Program Management
Microsoft Identity Division
#2 Choosing the right authentication method
Hi everyone, I’m Swaroop Krishnamurthy and I’m excited to share more with you about each method and what we’ve learned in the process.
What are the different authentication methods?
There are really two options for authentication in a hybrid environment, no matter how complex your organization: you can choose to authenticate in the cloud or you can authenticate on-premises.
If you choose to have your cloud identity service handle the authentication processwhich, for many organizations, is the easiest and more secure option (and I’ll tell you why below)there are a couple methods that we offer in Azure Active Directory (Azure AD).
The first one is what we call Password Hash Sync. In this method, a hash value of the user’s password is extracted and synchronized in Azure AD to authenticate the user when they sign in from the cloud. They can use the same username and password from the on-premises environment to access cloud resources too. This helps IT because they don’t have to deploy any additional infrastructure to make it work in the cloud. This method also enables Azure AD Identity Protection capabilities, which protect and monitor your users’ passwords against leaked credential reports to prevent bad passwords from being used.
The second one is Pass-through Authentication. This method uses a software agent to connect to passwords stored on-premises for validation, so that users can sign in to cloud apps with the same username and password for on-premises resources. It’s a lightweight solution for IT and does not store any form of user passwords in the cloud, which may be a requirement for certain organizations. Like Password Hash Sync, pass-through authentication protects your on-premises accounts by working seamlessly with Azure AD conditional access policies, and it also supports Smart Lockout to prevent brute force attacks.
I’ve covered cloud authentication methods, but there’s another option for custom or complex authentication needs, called federated authentication.
With Federated Authentication, Azure AD will hand off the authentication process to a separate trusted authentication system, such as Active Directory Federation Services, to validate the user’s password or sign-in. This method makes sense for organizations with authentication requirements not currently available in Azure AD, such as legacy application protocols.
How do I choose?
For Azure AD customers, I’ve tried to simplify the decision with this decision tree below. It helps illustrate the effort, user experiences, advanced scenarios, business continuity and other considerations which you should incorporate into your decision-making process.
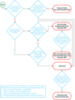
This decision tree is just a guideline. If you’d like to read more about each of the authentication methods and compare the pros and cons, check out the
Authentication methods documentation and comparison chart.
Regards,
Swaroop (Twitter: @swaroop_kmurthy)
Check out the other posts in this series:
Download theHybrid Identity Digital Transformation Framework whitepaper to get a baseline on your hybrid identity strategy.
Continue reading...
I’m here to share with you the next part in our Eight Essentials for Hybrid Identity blog series, based on what we’ve learned from working with tens of thousands of organizations on this hybrid journey. When setting up single sign-on for your employees and partners to all their SaaS applications and on-premises apps and resources, the first thing we want to do is establish identities in the cloud.
With identities as your control plane, authentication is the foundation for cloud access. Choosing the right authentication method is a crucial decision, but also one that’s different for every organization and might change over time.
To help walk you through this decision, I’ve invited Swaroop, the PM on my team working on these hybrid authentication technologies, to share his insight.
Best Regards,
Alex Simons (Twitter:@Alex_A_Simons)
Director of Program Management
Microsoft Identity Division
#2 Choosing the right authentication method
Hi everyone, I’m Swaroop Krishnamurthy and I’m excited to share more with you about each method and what we’ve learned in the process.
What are the different authentication methods?
There are really two options for authentication in a hybrid environment, no matter how complex your organization: you can choose to authenticate in the cloud or you can authenticate on-premises.
If you choose to have your cloud identity service handle the authentication processwhich, for many organizations, is the easiest and more secure option (and I’ll tell you why below)there are a couple methods that we offer in Azure Active Directory (Azure AD).
The first one is what we call Password Hash Sync. In this method, a hash value of the user’s password is extracted and synchronized in Azure AD to authenticate the user when they sign in from the cloud. They can use the same username and password from the on-premises environment to access cloud resources too. This helps IT because they don’t have to deploy any additional infrastructure to make it work in the cloud. This method also enables Azure AD Identity Protection capabilities, which protect and monitor your users’ passwords against leaked credential reports to prevent bad passwords from being used.
The second one is Pass-through Authentication. This method uses a software agent to connect to passwords stored on-premises for validation, so that users can sign in to cloud apps with the same username and password for on-premises resources. It’s a lightweight solution for IT and does not store any form of user passwords in the cloud, which may be a requirement for certain organizations. Like Password Hash Sync, pass-through authentication protects your on-premises accounts by working seamlessly with Azure AD conditional access policies, and it also supports Smart Lockout to prevent brute force attacks.
I’ve covered cloud authentication methods, but there’s another option for custom or complex authentication needs, called federated authentication.
With Federated Authentication, Azure AD will hand off the authentication process to a separate trusted authentication system, such as Active Directory Federation Services, to validate the user’s password or sign-in. This method makes sense for organizations with authentication requirements not currently available in Azure AD, such as legacy application protocols.
How do I choose?
For Azure AD customers, I’ve tried to simplify the decision with this decision tree below. It helps illustrate the effort, user experiences, advanced scenarios, business continuity and other considerations which you should incorporate into your decision-making process.

This decision tree is just a guideline. If you’d like to read more about each of the authentication methods and compare the pros and cons, check out the
Authentication methods documentation and comparison chart.
Regards,
Swaroop (Twitter: @swaroop_kmurthy)
Check out the other posts in this series:
Download theHybrid Identity Digital Transformation Framework whitepaper to get a baseline on your hybrid identity strategy.
Continue reading...