Server Man
Well-Known Member
- May 17, 2015

- Windows 7

- IE 11
Microsoft and Zscaler expand their security association with new capabilities using Microsoft EMS, including Microsoft Intune and Azure Active Directory (AAD). Customers using the Zscaler Application on Intune-managed iOS devices to establish VPN connections can now enjoy seamless deployment and configuration of the app. The new capability allows IT admins to provision the Zscaler app to specific AAD users or groups from within the Intune console, and configure connections by using the existing Intune VPN profile workflow.
Conditional access
When Zscaler Private Access (ZPA) is deployed together with Microsoft EMS, users can leverage conditional access for simple, on demand access to private applications without exposing internal networks. For example, a conditional access policy may be applied using Intune to require a particular device configuration (say, a passcode on the device) before granting access to the Zscaler remote access service. If the user does not set a passcode on their device, they are unable to access any ZPA applications. When the user sets a device passcode, the condition changes and the access is automatically remediated.
User experience is one of the most important factors in designing any solution for mobile users. If it is not frictionless and easy to use, users will not adopt it and may lose productivity while they find an alternative to continue their work. The benefit of this interoperability between EMS and Zscaler is that it maintains the familiar experience. There are no additional login portals, or more passwords to remember. Thanks to native integration with AAD authentication, the user simply logs into the same login page they always do and Zscaler App will leverage this authenticated session to identify the user whenever they send traffic through the Zscaler Cloud, or access private applications.
How it works
With Intune, pre-configuration of Zscaler App is simple. Once you’ve configured Zscaler App to deploy automatically to client iOS devices, create a VPN profile from the Intune console and enter your configuration items:
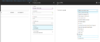 VPN profile in Intune console
VPN profile in Intune console
You may elect to configure a set of rules to determine when a VPN connection is automatically established, not established, or disconnected for the user’s device (on-demand VPN), or enable per-app VPN capability. The latter is particularly helpful where the device is owned by the user (BYOD) and you want to secure only the business applications on the device, without managing their personal accounts, apps, and data. Simply select the VPN type and this will let you configure the desired behavior:
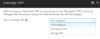 On-demand or per-app VPN
On-demand or per-app VPN
If conditional access is configured, and the user is not compliant, they see a reason why their access is denied and how they can be compliant again.
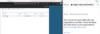 Conditional access policy applied
Conditional access policy applied
The key benefits of the expanded capabilities offered by this integration may be summarized as follows:
Read more about this capability here VPN settings for iOS devices in Microsoft Intune - Azure
Continue reading...
Conditional access
When Zscaler Private Access (ZPA) is deployed together with Microsoft EMS, users can leverage conditional access for simple, on demand access to private applications without exposing internal networks. For example, a conditional access policy may be applied using Intune to require a particular device configuration (say, a passcode on the device) before granting access to the Zscaler remote access service. If the user does not set a passcode on their device, they are unable to access any ZPA applications. When the user sets a device passcode, the condition changes and the access is automatically remediated.
User experience is one of the most important factors in designing any solution for mobile users. If it is not frictionless and easy to use, users will not adopt it and may lose productivity while they find an alternative to continue their work. The benefit of this interoperability between EMS and Zscaler is that it maintains the familiar experience. There are no additional login portals, or more passwords to remember. Thanks to native integration with AAD authentication, the user simply logs into the same login page they always do and Zscaler App will leverage this authenticated session to identify the user whenever they send traffic through the Zscaler Cloud, or access private applications.
How it works
With Intune, pre-configuration of Zscaler App is simple. Once you’ve configured Zscaler App to deploy automatically to client iOS devices, create a VPN profile from the Intune console and enter your configuration items:
You may elect to configure a set of rules to determine when a VPN connection is automatically established, not established, or disconnected for the user’s device (on-demand VPN), or enable per-app VPN capability. The latter is particularly helpful where the device is owned by the user (BYOD) and you want to secure only the business applications on the device, without managing their personal accounts, apps, and data. Simply select the VPN type and this will let you configure the desired behavior:
If conditional access is configured, and the user is not compliant, they see a reason why their access is denied and how they can be compliant again.
The key benefits of the expanded capabilities offered by this integration may be summarized as follows:
- Manage user and group access to Zscaler resources, from within the Microsoft device management console
- Automatically deploy and configure Zscaler App for iOS to deliver seamless user experience
- Provide single sign on (SSO) to authenticate both administrators and users for remote access to corporate resources
- Leverage ‘per-app VPN’ functionality or enable ‘on-demand VPN’ for the device
- Limit access to applications based on Intune and Azure AD conditional access policies
Read more about this capability here VPN settings for iOS devices in Microsoft Intune - Azure
Continue reading...