A
ATyler - Life Flight Network
Hello, I've inherited a network where the previous admin has deployed a single enterprise root CA onto an existing Domain Controller. Our only use for certificates today is simply to issue Domain Controller certificates so that our environment can support LDAPS, but down the road we may use it for other purposes. Anyway, I have a couple of questions regarding the process of standing up a new CA implementation in our same domain. Then finally removing the existing role entirely from the existing Domain Controller. Here it goes....
1. It appears the standard recommendation from M$ is to deploy an offline root CA that is not domain joined, then to deploy an enterprise subordinate CA that is domain joined. So I will plan to go that route.
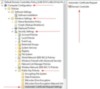
2. I notice that Domain Controllers automatically enroll for certificates if the root CA role is deployed onto an existing Domain Controller. Because I will be moving CA services off to a member server, what is the best way to ensure that Domain Controllers will enroll for certificates from the CA automatically? In the lab I have found the following setting that does the trick, is this the only option?
3. When you stand up a new enterprise CA that is hosted on a member server, is it necessary to use an AD GPO to distribute the root CA certificate to all of your windows desktop computers trusted root store? Or is there some behind the scenes mechanism that causes domain joined workstations to trust an enterprise CA automatically without having to distribute the root CA certificate via GPO?
4. I notice that the current certificate templates and root CA are currently listed in the directory. For example if you use ADSIEDIT to browse to Configuration > CN=Services > CN=PUblic Key Services, you will find templates under "CN=Certificate Templates" and your current root CA listed under "CN=Certificate Authorities".. Are these entries automatically removed when the CA role is uninstalled? Also, if I have two separate CA implementations in the same domain, how do existing domain controllers choose which CA to renew certificates from?
Continue reading...
1. It appears the standard recommendation from M$ is to deploy an offline root CA that is not domain joined, then to deploy an enterprise subordinate CA that is domain joined. So I will plan to go that route.
2. I notice that Domain Controllers automatically enroll for certificates if the root CA role is deployed onto an existing Domain Controller. Because I will be moving CA services off to a member server, what is the best way to ensure that Domain Controllers will enroll for certificates from the CA automatically? In the lab I have found the following setting that does the trick, is this the only option?

3. When you stand up a new enterprise CA that is hosted on a member server, is it necessary to use an AD GPO to distribute the root CA certificate to all of your windows desktop computers trusted root store? Or is there some behind the scenes mechanism that causes domain joined workstations to trust an enterprise CA automatically without having to distribute the root CA certificate via GPO?
4. I notice that the current certificate templates and root CA are currently listed in the directory. For example if you use ADSIEDIT to browse to Configuration > CN=Services > CN=PUblic Key Services, you will find templates under "CN=Certificate Templates" and your current root CA listed under "CN=Certificate Authorities".. Are these entries automatically removed when the CA role is uninstalled? Also, if I have two separate CA implementations in the same domain, how do existing domain controllers choose which CA to renew certificates from?
Continue reading...