Server Man
Well-Known Member
- May 17, 2015

- Windows 10

- IE 11
___________________________________________________________________________________________________________________________
IMPORTANT ANNOUNCEMENT FOR OUR READERS!
AskPFEPlat is in the process of a transformation to the new Core Infrastructure and Security TechCommunity, and will be moving by the end of March 2019 to our new home at Core Infrastructure and Security Blog - Microsoft Tech Community (hosted at https://techcommunity.microsoft.com). Please bear with us while we are still under construction!
We will continue bringing you the same great content, from the same great contributors, on our new platform. Until then, you can access our new content on either Ask Premier Field Engineering (PFE) Platforms as you do today, or at our new site Core Infrastructure and Security Blog - Microsoft Tech Community. Please feel free to update your bookmarks accordingly!
Why are we doing this? Simple really; we are looking to expand our team internally in order to provide you even more great content, as well as take on a more proactive role in the future with our readers (more to come on that later)! Since our team encompasses many more roles than Premier Field Engineers these days, we felt it was also time we reflected that initial expansion.
If you have never visited the TechCommunity site, it can be found at https://techcommunity.microsoft.com. On the TechCommunity site, you will find numerous technical communities across many topics, which include discussion areas, along with blog content.
NOTE: In addition to the AskPFEPlat-to-Core Infrastructure and Security transformation, Premier Field Engineers from all technology areas will be working together to expand the TechCommunity site even further, joining together in the technology agnostic Premier Field Engineering TechCommunity (along with Core Infrastructure and Security), which can be found at Premier Field Engineering - Microsoft Tech Community!
As always, thank you for continuing to read the Core Infrastructure and Security (AskPFEPlat) blog, and we look forward to providing you more great content well into the future!
__________________________________________________________________________________________________________________________
Introduction
Hello, my name is Richard McIver and I’m a Premier Field Engineer with Microsoft specializing in System Center Configuration Manager.
I was recently working with a customer who suddenly started receiving a strange KDC error when attempting to run Configuration Manager reports from either within the Administration Console or the Reporting Services web portal. It took quite a bit of troubleshooting to isolate the root cause, so I’d just like to share our findings and resolution steps.
Problem Description
When running Configuration Manager reports that rely on Role Based Access Control (RBAC), SQL Server Reporting Services (SSRS) will attempt to communicate with Active Directory via Kerberos authentication to resolve the Security Identifier (SID) of the user.
However, when this customer attempted to run reports with RBAC embedded, the following error was displayed and the report failed to load.
The DefaultValue expression for the report parameter ‘UserTokenSIDs’ contains an error: The encryption type requested is not supported by the KDC. (rsRuntimeErrorInExpression)
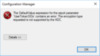
The customer environment was SQL Server 2016 Reporting Services running on Windows Server 2012 R2, however I’ve since been able to replicate this issue on Windows Server 2016 as well.
Root Cause Analysis
We eventually traced the root cause down to a security policy settings on the reporting point server that was recently configured via domain Group Policy Object (GPO).
Computer ConfigurationWindows SettingsSecurity SettingsLocal PoliciesSecurity OptionsNetwork security: Configure encryption types allowed for Kerberos: AES128_HMAC_SH1, AES256_HMAC_SHA1, Future encryption types selected
As configured, this setting has the effect of limiting the encryption types allowed for Kerberos authentication from the reporting point server to only AES128, AES256, and Future encryption types.
However, the service account used by the SQL Reporting Services service was not properly configured to support these algorithms. Instead, SSRS was attempting to authenticate using the RC4 encryption type, which is no longer allowed on the server, resulting in the KDC error.
Remediation
In this case, the error can be resolved in one of two ways.

Steps to configure the policy setting Network security: Configure encryption types allowed for Kerberos
Method 1 – Local Security Policy
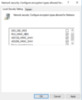
Method 2 – Group Policy Object (GPO)

And that’s about for now… Hopefully this helps you out, and thanks for reading!
References:
Continue reading...
IMPORTANT ANNOUNCEMENT FOR OUR READERS!
AskPFEPlat is in the process of a transformation to the new Core Infrastructure and Security TechCommunity, and will be moving by the end of March 2019 to our new home at Core Infrastructure and Security Blog - Microsoft Tech Community (hosted at https://techcommunity.microsoft.com). Please bear with us while we are still under construction!
We will continue bringing you the same great content, from the same great contributors, on our new platform. Until then, you can access our new content on either Ask Premier Field Engineering (PFE) Platforms as you do today, or at our new site Core Infrastructure and Security Blog - Microsoft Tech Community. Please feel free to update your bookmarks accordingly!
Why are we doing this? Simple really; we are looking to expand our team internally in order to provide you even more great content, as well as take on a more proactive role in the future with our readers (more to come on that later)! Since our team encompasses many more roles than Premier Field Engineers these days, we felt it was also time we reflected that initial expansion.
If you have never visited the TechCommunity site, it can be found at https://techcommunity.microsoft.com. On the TechCommunity site, you will find numerous technical communities across many topics, which include discussion areas, along with blog content.
NOTE: In addition to the AskPFEPlat-to-Core Infrastructure and Security transformation, Premier Field Engineers from all technology areas will be working together to expand the TechCommunity site even further, joining together in the technology agnostic Premier Field Engineering TechCommunity (along with Core Infrastructure and Security), which can be found at Premier Field Engineering - Microsoft Tech Community!
As always, thank you for continuing to read the Core Infrastructure and Security (AskPFEPlat) blog, and we look forward to providing you more great content well into the future!
__________________________________________________________________________________________________________________________
Introduction
Hello, my name is Richard McIver and I’m a Premier Field Engineer with Microsoft specializing in System Center Configuration Manager.
I was recently working with a customer who suddenly started receiving a strange KDC error when attempting to run Configuration Manager reports from either within the Administration Console or the Reporting Services web portal. It took quite a bit of troubleshooting to isolate the root cause, so I’d just like to share our findings and resolution steps.
Problem Description
When running Configuration Manager reports that rely on Role Based Access Control (RBAC), SQL Server Reporting Services (SSRS) will attempt to communicate with Active Directory via Kerberos authentication to resolve the Security Identifier (SID) of the user.
However, when this customer attempted to run reports with RBAC embedded, the following error was displayed and the report failed to load.
The DefaultValue expression for the report parameter ‘UserTokenSIDs’ contains an error: The encryption type requested is not supported by the KDC. (rsRuntimeErrorInExpression)

The customer environment was SQL Server 2016 Reporting Services running on Windows Server 2012 R2, however I’ve since been able to replicate this issue on Windows Server 2016 as well.
Root Cause Analysis
We eventually traced the root cause down to a security policy settings on the reporting point server that was recently configured via domain Group Policy Object (GPO).
Computer ConfigurationWindows SettingsSecurity SettingsLocal PoliciesSecurity OptionsNetwork security: Configure encryption types allowed for Kerberos: AES128_HMAC_SH1, AES256_HMAC_SHA1, Future encryption types selected
As configured, this setting has the effect of limiting the encryption types allowed for Kerberos authentication from the reporting point server to only AES128, AES256, and Future encryption types.
However, the service account used by the SQL Reporting Services service was not properly configured to support these algorithms. Instead, SSRS was attempting to authenticate using the RC4 encryption type, which is no longer allowed on the server, resulting in the KDC error.
Remediation
In this case, the error can be resolved in one of two ways.
- Enable AES 128-bit and/or AES 256-bit encryption for the SQL Reporting Services service account
- Configure the Network security: Configure encryption types allowed for Kerberos policy setting on the reporting point server to include the RC4_HMAC_MD5 encryption type
- Open Active Directory Users and Computers
- Browse to the user account used by SQL Reporting Services on the affected server
- Right-click the user account and select Properties
- Click on the Account tab
- Under Account options, check the box next to one or both of the following
- This account supports Kerberos AES 128 bit encryption
- This account supports Kerberos AES 256 bit encryption
- Click OK
Steps to configure the policy setting Network security: Configure encryption types allowed for Kerberos
Method 1 – Local Security Policy
- On the affected server, open an elevated command prompt
- Type SECPOL and hit Enter
- In the Local Security Policy management console, expand Local Policies and click on Security Options
- Scroll down in the let-hand pane until you find the setting Network security: Configure encryption types allowed for Kerberos
- Right-click this setting and select Properties
- In the Local Security Settings tab, check the box next to RC4_HMAC_MD5, AES128_HMAC_SHA1, AES256_HMAC_SHA1, and Future encryption types
- Click OK

Method 2 – Group Policy Object (GPO)
- Open the Group Policy Management console and edit a new or existing GPO
- In the Group Policy Management Editor, expand Computer ConfigurationPoliciesWindows SettingsSecurity SettingsLocal PoliciesSecurity Options
- Right-click on Network security: Configure encryption types allowed for Kerberos and click Properties
- On the Security Policy Setting tab, check the box to Define these policy settings
- Check the box next to RC4_HMAC_MD5, AES128_HMAC_SHA1, AES256_HMAC_SHA1, and Future encryption types
- Click OK

And that’s about for now… Hopefully this helps you out, and thanks for reading!
References:
- Windows Configurations for Kerberos Supported Encryption Type
- https://docs.microsoft.com/en-us/wi...nfigure-encryption-types-allowed-for-kerberos
Continue reading...