K
Keith Petite
I have been experiencing a series of BSODs since the 19h1 update on Nov 12th. At first I thought it was hardware related, so I started swapping memory chips and GPUs... no fix that way.
Then I started watching my event viewer and noticed a trend related to my AMD Processor. I am running a non-OC AMD 2700X, with 32G of DDR4 at 2133 stock, again no-OC. I had an issue with the Chipset (ASMEDIA) interferring with my Commander Pro RGB Controller, so I pulled the USB Cable, but the BSODs continued. There were multiple Errors in the Event Viewer for the Corsair device, but that is a known problem with the ASMEDIA Driver Set, so I will be replacing the Motherboard to fix that issue. (meh)
Today I crashed again, but no BSOD this time. It was really weird - I attempted to move (drag) a folder from my right monitor to my left monitor, and as I let go of the folder to complete the Move, the computer black screened on me, with no response from the KB or Mouse. Caps-Lock did not light up at all. hmmm.... So, I waited a minute, and then just shut her down with the PSU Switch.
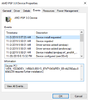
So, I went into research mode and found my way back to the Event Viewer and my Minidump folder. DL'd WinDbg and began reading the details on debugging. That's beyond my scope, so I throw it up for the MS Team analyze. My last official BSOD that created a dmp file was 23 Nov 2019, so here it is below. I have also included some interesting screenshots of things I do not understand that appear relative to the problem, however I do not know how to repair the problem.
Special Notes: This is a fresh install of Win10 Pro on an EVO 970Pro 500gb (nvme) No other hardware changes have taken place in 8 months. No other BSODs on my other SSD, this all begain after the 19h1 update.
Microsoft (R) Windows Debugger Version 10.0.19494.1001 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\112319-7781-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: srv*
Executable search path is:
Windows 10 Kernel Version 18362 MP (16 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 18362.1.amd64fre.19h1_release.190318-1202
Machine Name:
Kernel base = 0xfffff807`2f000000 PsLoadedModuleList = 0xfffff807`2f448170
Debug session time: Sat Nov 23 23:23:13.252 2019 (UTC - 6:00)
System Uptime: 0 days 2:31:28.938
Loading Kernel Symbols
...............................................................
................................................................
...........................................................
Loading User Symbols
Loading unloaded module list
......
For analysis of this file, run !analyze -v
nt!KeBugCheckEx:
fffff807`2f1c14e0 48894c2408 mov qword ptr [rsp+8],rcx ss:0018:ffff9084`3dae6550=000000000000000a
11: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 0000000000000004, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000001, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff8072f1c88af, address which referenced memory
Debugging Details:
------------------
*** WARNING: Unable to verify checksum for win32k.sys
KEY_VALUES_STRING: 1
Key : Analysis.CPU.Sec
Value: 3
Key : Analysis.DebugAnalysisProvider.CPP
Value: Create: 8007007e on DESKTOP-AUCNKUU
Key : Analysis.DebugData
Value: CreateObject
Key : Analysis.DebugModel
Value: CreateObject
Key : Analysis.Elapsed.Sec
Value: 13
Key : Analysis.Memory.CommitPeak.Mb
Value: 70
Key : Analysis.System
Value: CreateObject
BUGCHECK_CODE: a
BUGCHECK_P1: 4
BUGCHECK_P2: 2
BUGCHECK_P3: 1
BUGCHECK_P4: fffff8072f1c88af
WRITE_ADDRESS: fffff8072f5733b8: Unable to get MiVisibleState
Unable to get NonPagedPoolStart
Unable to get NonPagedPoolEnd
Unable to get PagedPoolStart
Unable to get PagedPoolEnd
fffff8072f42a3c8: Unable to get Flags value from nt!KdVersionBlock
fffff8072f42a3c8: Unable to get Flags value from nt!KdVersionBlock
unable to get nt!MmSpecialPagesInUse
0000000000000004
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: System
TRAP_FRAME: ffff90843dae6690 -- (.trap 0xffff90843dae6690)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000004 rbx=0000000000000000 rcx=ffff90843dae6cc0
rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff8072f1c88af rsp=ffff90843dae6820 rbp=00000067b4bbbdff
r8=000000010000002d r9=0000000000000000 r10=ffff800200a88180
r11=ffffa18d3b080080 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl zr ac po cy
nt!SwapContext+0x36f:
fffff807`2f1c88af 0fc719 xrstors [rcx]
Resetting default scope
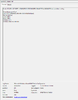
STACK_TEXT:
ffff9084`3dae6548 fffff807`2f1d32e9 : 00000000`0000000a 00000000`00000004 00000000`00000002 00000000`00000001 : nt!KeBugCheckEx
ffff9084`3dae6550 fffff807`2f1cf62b : ffffa18d`4749e010 ffffa18d`00000000 ffffa18d`49b25470 ffffa18d`43fa2df0 : nt!KiBugCheckDispatch+0x69
ffff9084`3dae6690 fffff807`2f1c88af : 00000067`b4bbbdff 00000000`00000001 ffff8002`00000000 00000001`0000002d : nt!KiPageFault+0x46b
ffff9084`3dae6820 fffff807`2f1c8266 : 00000000`00000000 00000000`00000001 00000000`000009c8 ffffa18d`4a1d6400 : nt!SwapContext+0x36f
ffff9084`3dae6860 fffff807`2f03c7bd : ffff8002`00a88180 ffffa18d`fffffffe ffff8002`ffffffff 00000000`00000001 : nt!KiSwapContext+0x76
ffff9084`3dae69a0 fffff807`2f03b644 : ffffa18d`490a7040 fffff807`00000000 ffffa18d`00000000 00000000`00000000 : nt!KiSwapThread+0xbfd
ffff9084`3dae6a40 fffff807`2f0bd96c : ffffa18d`47652040 00000000`00000000 fffff807`405b5800 ffffa18d`490a7180 : nt!KiCommitThreadWait+0x144
ffff9084`3dae6ae0 fffff807`2f0bd450 : ffffa18d`3b1029e0 ffffa18d`490a7000 fffff807`2f067b00 ffff9f58`00000008 : nt!KeRemovePriQueue+0x25c
ffff9084`3dae6b70 fffff807`2f12a7a5 : ffffa18d`490a7040 00000000`00000080 ffffa18d`3b080080 ffff9f1d`00000001 : nt!ExpWorkerThread+0xa0
ffff9084`3dae6c10 fffff807`2f1c8b2a : ffff8002`00896180 ffffa18d`490a7040 fffff807`2f12a750 00000000`00000064 : nt!PspSystemThreadStartup+0x55
ffff9084`3dae6c60 00000000`00000000 : ffff9084`3dae7000 ffff9084`3dae1000 00000000`00000000 00000000`00000000 : nt!KiStartSystemThread+0x2a
SYMBOL_NAME: nt!SwapContext+36f
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
IMAGE_VERSION: 10.0.18362.476
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: 36f
FAILURE_BUCKET_ID: AV_nt!SwapContext
OS_VERSION: 10.0.18362.1
BUILDLAB_STR: 19h1_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {47b746a3-60bf-1f5a-5fa5-88903b6a3204}
Followup: MachineOwner
---------
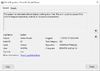
Tonight's hard-crash screenshot is below, here are the details:
- <Event xmlns=" ">
- <System>
<Provider Name="Microsoft-Windows-Kernel-Power" Guid="{331c3b3a-2005-44c2-ac5e-77220c37d6b4}" />
<EventID>41</EventID>
<Version>6</Version>
<Level>1</Level>
<Task>63</Task>
<Opcode>0</Opcode>
<Keywords>0x8000400000000002</Keywords>
<TimeCreated SystemTime="2019-11-28T01:20:52.011176700Z" />
<EventRecordID>3532</EventRecordID>
<Correlation />
<Execution ProcessID="4" ThreadID="8" />
<Channel>System</Channel>
<Computer>DESKTOP-AUCNKUU</Computer>
<Security UserID="S-1-5-18" />
</System>
- <EventData>
<Data Name="BugcheckCode">0</Data>
<Data Name="BugcheckParameter1">0x0</Data>
<Data Name="BugcheckParameter2">0x0</Data>
<Data Name="BugcheckParameter3">0x0</Data>
<Data Name="BugcheckParameter4">0x0</Data>
<Data Name="SleepInProgress">0</Data>
<Data Name="PowerButtonTimestamp">0</Data>
<Data Name="BootAppStatus">0</Data>
<Data Name="Checkpoint">41</Data>
<Data Name="ConnectedStandbyInProgress">false</Data>
<Data Name="SystemSleepTransitionsToOn">1</Data>
<Data Name="CsEntryScenarioInstanceId">0</Data>
<Data Name="BugcheckInfoFromEFI">false</Data>
<Data Name="CheckpointStatus">0</Data>
</EventData>
</Event>
Seeking your guidance and wisdom as this is obviously a deeper issue and a bad driver.
TIA
Continue reading...
Then I started watching my event viewer and noticed a trend related to my AMD Processor. I am running a non-OC AMD 2700X, with 32G of DDR4 at 2133 stock, again no-OC. I had an issue with the Chipset (ASMEDIA) interferring with my Commander Pro RGB Controller, so I pulled the USB Cable, but the BSODs continued. There were multiple Errors in the Event Viewer for the Corsair device, but that is a known problem with the ASMEDIA Driver Set, so I will be replacing the Motherboard to fix that issue. (meh)
Today I crashed again, but no BSOD this time. It was really weird - I attempted to move (drag) a folder from my right monitor to my left monitor, and as I let go of the folder to complete the Move, the computer black screened on me, with no response from the KB or Mouse. Caps-Lock did not light up at all. hmmm.... So, I waited a minute, and then just shut her down with the PSU Switch.
So, I went into research mode and found my way back to the Event Viewer and my Minidump folder. DL'd WinDbg and began reading the details on debugging. That's beyond my scope, so I throw it up for the MS Team analyze. My last official BSOD that created a dmp file was 23 Nov 2019, so here it is below. I have also included some interesting screenshots of things I do not understand that appear relative to the problem, however I do not know how to repair the problem.
Special Notes: This is a fresh install of Win10 Pro on an EVO 970Pro 500gb (nvme) No other hardware changes have taken place in 8 months. No other BSODs on my other SSD, this all begain after the 19h1 update.
Microsoft (R) Windows Debugger Version 10.0.19494.1001 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Loading Dump File [C:\Windows\Minidump\112319-7781-01.dmp]
Mini Kernel Dump File: Only registers and stack trace are available
Symbol search path is: srv*
Executable search path is:
Windows 10 Kernel Version 18362 MP (16 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Built by: 18362.1.amd64fre.19h1_release.190318-1202
Machine Name:
Kernel base = 0xfffff807`2f000000 PsLoadedModuleList = 0xfffff807`2f448170
Debug session time: Sat Nov 23 23:23:13.252 2019 (UTC - 6:00)
System Uptime: 0 days 2:31:28.938
Loading Kernel Symbols
...............................................................
................................................................
...........................................................
Loading User Symbols
Loading unloaded module list
......
For analysis of this file, run !analyze -v
nt!KeBugCheckEx:
fffff807`2f1c14e0 48894c2408 mov qword ptr [rsp+8],rcx ss:0018:ffff9084`3dae6550=000000000000000a
11: kd> !analyze -v
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 0000000000000004, memory referenced
Arg2: 0000000000000002, IRQL
Arg3: 0000000000000001, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff8072f1c88af, address which referenced memory
Debugging Details:
------------------
*** WARNING: Unable to verify checksum for win32k.sys
KEY_VALUES_STRING: 1
Key : Analysis.CPU.Sec
Value: 3
Key : Analysis.DebugAnalysisProvider.CPP
Value: Create: 8007007e on DESKTOP-AUCNKUU
Key : Analysis.DebugData
Value: CreateObject
Key : Analysis.DebugModel
Value: CreateObject
Key : Analysis.Elapsed.Sec
Value: 13
Key : Analysis.Memory.CommitPeak.Mb
Value: 70
Key : Analysis.System
Value: CreateObject
BUGCHECK_CODE: a
BUGCHECK_P1: 4
BUGCHECK_P2: 2
BUGCHECK_P3: 1
BUGCHECK_P4: fffff8072f1c88af
WRITE_ADDRESS: fffff8072f5733b8: Unable to get MiVisibleState
Unable to get NonPagedPoolStart
Unable to get NonPagedPoolEnd
Unable to get PagedPoolStart
Unable to get PagedPoolEnd
fffff8072f42a3c8: Unable to get Flags value from nt!KdVersionBlock
fffff8072f42a3c8: Unable to get Flags value from nt!KdVersionBlock
unable to get nt!MmSpecialPagesInUse
0000000000000004
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: System
TRAP_FRAME: ffff90843dae6690 -- (.trap 0xffff90843dae6690)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000000004 rbx=0000000000000000 rcx=ffff90843dae6cc0
rdx=0000000000000000 rsi=0000000000000000 rdi=0000000000000000
rip=fffff8072f1c88af rsp=ffff90843dae6820 rbp=00000067b4bbbdff
r8=000000010000002d r9=0000000000000000 r10=ffff800200a88180
r11=ffffa18d3b080080 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl zr ac po cy
nt!SwapContext+0x36f:
fffff807`2f1c88af 0fc719 xrstors [rcx]
Resetting default scope
STACK_TEXT:
ffff9084`3dae6548 fffff807`2f1d32e9 : 00000000`0000000a 00000000`00000004 00000000`00000002 00000000`00000001 : nt!KeBugCheckEx
ffff9084`3dae6550 fffff807`2f1cf62b : ffffa18d`4749e010 ffffa18d`00000000 ffffa18d`49b25470 ffffa18d`43fa2df0 : nt!KiBugCheckDispatch+0x69
ffff9084`3dae6690 fffff807`2f1c88af : 00000067`b4bbbdff 00000000`00000001 ffff8002`00000000 00000001`0000002d : nt!KiPageFault+0x46b
ffff9084`3dae6820 fffff807`2f1c8266 : 00000000`00000000 00000000`00000001 00000000`000009c8 ffffa18d`4a1d6400 : nt!SwapContext+0x36f
ffff9084`3dae6860 fffff807`2f03c7bd : ffff8002`00a88180 ffffa18d`fffffffe ffff8002`ffffffff 00000000`00000001 : nt!KiSwapContext+0x76
ffff9084`3dae69a0 fffff807`2f03b644 : ffffa18d`490a7040 fffff807`00000000 ffffa18d`00000000 00000000`00000000 : nt!KiSwapThread+0xbfd
ffff9084`3dae6a40 fffff807`2f0bd96c : ffffa18d`47652040 00000000`00000000 fffff807`405b5800 ffffa18d`490a7180 : nt!KiCommitThreadWait+0x144
ffff9084`3dae6ae0 fffff807`2f0bd450 : ffffa18d`3b1029e0 ffffa18d`490a7000 fffff807`2f067b00 ffff9f58`00000008 : nt!KeRemovePriQueue+0x25c
ffff9084`3dae6b70 fffff807`2f12a7a5 : ffffa18d`490a7040 00000000`00000080 ffffa18d`3b080080 ffff9f1d`00000001 : nt!ExpWorkerThread+0xa0
ffff9084`3dae6c10 fffff807`2f1c8b2a : ffff8002`00896180 ffffa18d`490a7040 fffff807`2f12a750 00000000`00000064 : nt!PspSystemThreadStartup+0x55
ffff9084`3dae6c60 00000000`00000000 : ffff9084`3dae7000 ffff9084`3dae1000 00000000`00000000 00000000`00000000 : nt!KiStartSystemThread+0x2a
SYMBOL_NAME: nt!SwapContext+36f
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
IMAGE_VERSION: 10.0.18362.476
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: 36f
FAILURE_BUCKET_ID: AV_nt!SwapContext
OS_VERSION: 10.0.18362.1
BUILDLAB_STR: 19h1_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {47b746a3-60bf-1f5a-5fa5-88903b6a3204}
Followup: MachineOwner
---------
Tonight's hard-crash screenshot is below, here are the details:
- <Event xmlns=" ">
- <System>
<Provider Name="Microsoft-Windows-Kernel-Power" Guid="{331c3b3a-2005-44c2-ac5e-77220c37d6b4}" />
<EventID>41</EventID>
<Version>6</Version>
<Level>1</Level>
<Task>63</Task>
<Opcode>0</Opcode>
<Keywords>0x8000400000000002</Keywords>
<TimeCreated SystemTime="2019-11-28T01:20:52.011176700Z" />
<EventRecordID>3532</EventRecordID>
<Correlation />
<Execution ProcessID="4" ThreadID="8" />
<Channel>System</Channel>
<Computer>DESKTOP-AUCNKUU</Computer>
<Security UserID="S-1-5-18" />
</System>
- <EventData>
<Data Name="BugcheckCode">0</Data>
<Data Name="BugcheckParameter1">0x0</Data>
<Data Name="BugcheckParameter2">0x0</Data>
<Data Name="BugcheckParameter3">0x0</Data>
<Data Name="BugcheckParameter4">0x0</Data>
<Data Name="SleepInProgress">0</Data>
<Data Name="PowerButtonTimestamp">0</Data>
<Data Name="BootAppStatus">0</Data>
<Data Name="Checkpoint">41</Data>
<Data Name="ConnectedStandbyInProgress">false</Data>
<Data Name="SystemSleepTransitionsToOn">1</Data>
<Data Name="CsEntryScenarioInstanceId">0</Data>
<Data Name="BugcheckInfoFromEFI">false</Data>
<Data Name="CheckpointStatus">0</Data>
</EventData>
</Event>



Seeking your guidance and wisdom as this is obviously a deeper issue and a bad driver.
TIA
Continue reading...