Server Man
Well-Known Member
- May 17, 2015

- Windows 10

- Firefox 68.0
In a modern workplace where the average enterprise is using over 1,500 different cloud apps, and more than 80 gigabytes of data is being uploaded monthly to risky apps from business endpoint devices, the ability of IT and compliance administrators to manage and monitor shadow IT becomes an (almost) impossible mission. It is not only about the ability to assess the potential risk that cloud apps pose to the company, but also about the tools IT has (or doesn’t have) to control and manage access to these apps.
Complex network security solutions, time-consuming workflows for creating custom blocking rules, and a lot of manual work that needs to be done, make a simple process such as taking a list of cloud apps to be blocked and pushing these to web filtering rules a significant undertaking! When administrators have to manage too many personas and components in this process, it will dramatically slow them down when it comes to applying cloud app access policies in their organization.
In the last two years, Microsoft Defender Advanced Threat Protection (ATP) and Microsoft Cloud App Security have worked to build a full shadow IT discovery solution that analyzes organization’s traffic data against the Cloud App Security cloud app catalog. Apps are carefully curated to be included in this catalog and ranked and scored based on more than 90 risk factors to provide your organization with ongoing visibility into cloud app usage, existing shadow IT, and the risk shadow IT poses into your organization.
reporting of existing shadow IT, and to allow organizations to proactively take action on the high risk posed by use of these unsanctioned applications – thereby removing any further risk and usage across your business. This new feature, now in public preview, leverages Microsoft Defender ATP network protection in block mode ensuring the protections are in place wherever the device travels – in distributed offices, at airports, or at the local coffee shop.
By tagging apps in Cloud App Security as unsanctioned based on the comprehensive usage and risk assessment of each app that we provide, those risky app domains are then pushed to Microsoft Defender ATP as custom network indicators in near real-time.
This is a single-click control that can significantly improve security posture and save time.

Figure 1: Configure a cloud app as unsanctioned in one click
The process can also be completed manually, by reviewing discovered apps in your tenant and marking them as unsanctioned, or automatically by creating a cloud app control policy to block cloud apps that meet predefined conditions. For instance, in the Cloud App Security portal, you can now create a policy to automatically block access to non-compliant cloud storage apps, for example apps that do not comply with HIPAA and SOC 2 AND that are not Microsoft OneDrive for Business or Dropbox. Alternatively, you might want to block end users from accessing specific social networks in case there was a high volume of data upload identified. This can also be done manually or by creating a simple policy to handle blocking those network connections automatically.
The corresponding URL/Domains Indicators will appear in the “Microsoft Defender ATP Indicators” setting page under URLs/Domains tab.
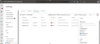
Figure 2: URL and Domain Indicators
When the user next attempts to access the unsanctioned app, they will be blocked by Windows Defender SmartScreen, and will not able to access the requested cloud resource.

Figure 3: Example user experience when attempting to access an unsanctioned app
Every instance of an endpoint trying to access a blocked cloud app will result in an informational alert in Microsoft Defender Security Center allowing you to drill down into the full machine timeline to see whether the endpoint was trying to access additional risky resources and to eliminate any concern of malicious behavior or data exfiltration attempts.
Microsoft Defender ATP and Cloud App Security together deliver this simple, powerful and unique outcome to ensure your modern workplace allows high end user productivity without neglecting your security principles, and to also allow you as an administrator to be more productive by setting automated policy-based flows to protect against user access to risky cloud resources. This enables you to put your limited resources on managing your security strategy, while we take care of operating and configurating your environment.
The Microsoft Defender ATP and Cloud App Security product teams would love to get your feedback on your overall experience with this feature, use this form to fill in your feedback.
Get Started in 3 quick steps
After you have verified that you have all the integration prerequisites listed in this article, follow the steps below to start blocking access to unsanctioned apps with Cloud App Security and Microsoft Defender ATP –
Step 1
In Microsoft Defender Security Center under Settings > Advanced features, enable Microsoft Cloud App Security integration:
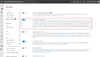
Step 2
In Microsoft Defender Security Center under Settings > Advanced features, enable Custom network indicators:
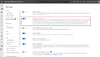
Step 3
In the Microsoft Cloud App Security portal under Settings > Microsoft Defender ATP integration, mark the checkbox to enable blocking of endpoint access to cloud apps marked as unsanctioned in Cloud App Security:

More info and feedback
Please let and know any questions you have!
Thank you
on behalf of Microsoft Defender ATP and Cloud App Security teams.
Continue reading...
Complex network security solutions, time-consuming workflows for creating custom blocking rules, and a lot of manual work that needs to be done, make a simple process such as taking a list of cloud apps to be blocked and pushing these to web filtering rules a significant undertaking! When administrators have to manage too many personas and components in this process, it will dramatically slow them down when it comes to applying cloud app access policies in their organization.
In the last two years, Microsoft Defender Advanced Threat Protection (ATP) and Microsoft Cloud App Security have worked to build a full shadow IT discovery solution that analyzes organization’s traffic data against the Cloud App Security cloud app catalog. Apps are carefully curated to be included in this catalog and ranked and scored based on more than 90 risk factors to provide your organization with ongoing visibility into cloud app usage, existing shadow IT, and the risk shadow IT poses into your organization.
reporting of existing shadow IT, and to allow organizations to proactively take action on the high risk posed by use of these unsanctioned applications – thereby removing any further risk and usage across your business. This new feature, now in public preview, leverages Microsoft Defender ATP network protection in block mode ensuring the protections are in place wherever the device travels – in distributed offices, at airports, or at the local coffee shop.
By tagging apps in Cloud App Security as unsanctioned based on the comprehensive usage and risk assessment of each app that we provide, those risky app domains are then pushed to Microsoft Defender ATP as custom network indicators in near real-time.
This is a single-click control that can significantly improve security posture and save time.
Figure 1: Configure a cloud app as unsanctioned in one click
The process can also be completed manually, by reviewing discovered apps in your tenant and marking them as unsanctioned, or automatically by creating a cloud app control policy to block cloud apps that meet predefined conditions. For instance, in the Cloud App Security portal, you can now create a policy to automatically block access to non-compliant cloud storage apps, for example apps that do not comply with HIPAA and SOC 2 AND that are not Microsoft OneDrive for Business or Dropbox. Alternatively, you might want to block end users from accessing specific social networks in case there was a high volume of data upload identified. This can also be done manually or by creating a simple policy to handle blocking those network connections automatically.
The corresponding URL/Domains Indicators will appear in the “Microsoft Defender ATP Indicators” setting page under URLs/Domains tab.
Figure 2: URL and Domain Indicators
When the user next attempts to access the unsanctioned app, they will be blocked by Windows Defender SmartScreen, and will not able to access the requested cloud resource.

Figure 3: Example user experience when attempting to access an unsanctioned app
Every instance of an endpoint trying to access a blocked cloud app will result in an informational alert in Microsoft Defender Security Center allowing you to drill down into the full machine timeline to see whether the endpoint was trying to access additional risky resources and to eliminate any concern of malicious behavior or data exfiltration attempts.
Microsoft Defender ATP and Cloud App Security together deliver this simple, powerful and unique outcome to ensure your modern workplace allows high end user productivity without neglecting your security principles, and to also allow you as an administrator to be more productive by setting automated policy-based flows to protect against user access to risky cloud resources. This enables you to put your limited resources on managing your security strategy, while we take care of operating and configurating your environment.
The Microsoft Defender ATP and Cloud App Security product teams would love to get your feedback on your overall experience with this feature, use this form to fill in your feedback.
Get Started in 3 quick steps
After you have verified that you have all the integration prerequisites listed in this article, follow the steps below to start blocking access to unsanctioned apps with Cloud App Security and Microsoft Defender ATP –
Step 1
In Microsoft Defender Security Center under Settings > Advanced features, enable Microsoft Cloud App Security integration:

Step 2
In Microsoft Defender Security Center under Settings > Advanced features, enable Custom network indicators:

Step 3
In the Microsoft Cloud App Security portal under Settings > Microsoft Defender ATP integration, mark the checkbox to enable blocking of endpoint access to cloud apps marked as unsanctioned in Cloud App Security:
More info and feedback
- Get started with our technical documentation
- Haven’t tried Microsoft Cloud App Security yet? Start a free trial today.
- As always, we want to hear from you! If you have any suggestions, questions, or comments, please visit us on our MCAS Tech Community page, Microsoft Defender ATP Tech community
- For more resources and information go to Cloud App Security website, or Microsoft Defender ATP community to learn more.
- “Shadow IT discovery & control with Microsoft Defender ATP and Cloud App Security” video – View: https://www.youtube.com/watch?v=kNclPOnbUNA
Please let and know any questions you have!
Thank you
on behalf of Microsoft Defender ATP and Cloud App Security teams.
Continue reading...