R
RoySasabe
The server threat landscape is constantly evolving with cybercriminals becoming more ambitious and sophisticated in their attacks, and the damage is becoming more costly to those targeted. In April 2022, the ransomware group Conti carried out two massive ransomware attacks that breached the Costa Rican government and affected nearly 30 different ministries and different essential services within the country. This attack was so disruptive that the President of Costa Rica had to declare a state of National Emergency, the first ever such instance in response to a cyberattack. In different incidents, Shields Health Care Group had a data breach where nearly 2 million patient records were stolen by attackers, and Medibank Private Ltd., one of the largest health insurance providers in Australia had data pertaining to 9.7 million customers stolen. In the latter case, the attackers threatened to release the customer data on the dark web unless a ransom was paid.
Servers are the backbone of modern businesses, and they store and process vast amounts of sensitive data. As a result, server security is critical to protect against cyberattacks that can cause financial losses, reputational damage, and legal liabilities. In 2021, Microsoft announced the launch of Secured-core servers in partnership with our silicon partners and original equipment manufacturers (OEMs). These servers offer some of the most advanced hardware-based security capabilities that make it harder for adversaries to carry out cyberattacks. In this post, we will provide an example of how the upcoming Windows Server 2025 Secured-core servers seamlessly integrate with the broader suite of Microsoft's security offerings to not just identify but also help block real world attacks.
There is an entire class of attacks that rely on an attack technique known as "Bring Your Own Vulnerable Driver" (BYOVD). In these attacks, a malicious adversary with administrative privileges installs a legitimately signed driver with a vulnerability in it on the target system. These drivers have direct access to the internals of the operating system. This vulnerability is then exploited to provide the attacker with the highest level of privileges on the system, which is then used to disable security processes running on the system. We'll now take a couple of vulnerable drivers that have been used in attacks in the past.
kprocesshacker.sys
Process Hacker is a free and open-source malware analysis tool that is used for debugging, malware detection and system monitoring. Process Hacker was used by a ransomware known as DoppelPaymer, which had several high-profile targets such as Foxconn, Kia and Boyce Technologies. DoppelPaymer hijacks ProcessHacker to terminate a list of processes such as those responsible for security, e-mail server, backup and database software to impair defenses. It drops the ProcessHacker executable, its driver and a malicious stager DLL into a subdirectory of %APPDATA%. The driver, known as kprocesshacker.sys, allows it to communicate with the kernel and is used to load the stager DLL via DLL Search Order Hijacking and subsequently, upon receiving a trigger, terminate processes running in the kernel.
asWarPot.sys
AvosLocker is a ransomware group that has targeted victims across multiple critical infrastructure sectors in the United States such as financial services and government facilities sectors. Certain samples of the AvosLocker Ransomware used a legitimate but vulnerable Avast Anti-Rootkit driver known as asWarPot.sys to disable endpoint protection agents and security features on the targeted systems.
Configuring your on-premises servers for hybrid cloud security is made simple with Windows Server 2025. Using the Azure Arc installer wizard included in Windows Server 2025, then onboarding with Microsoft Defender for Cloud will add cloud-based protections to Secured-core servers such as continuous assessment, built-in benchmarks, security recommendations, threat protection capabilities and remediation guidance in case threats have been detected. Here we will discuss how each layer of security works to help protect against threats.
Secured-core servers offer a hardware-based security feature known as Hypervisor-protected code integrity (HVCI). HVCI uses Virtualization-based Security (VBS) to run kernel mode code integrity inside a secure, isolated environment instead of the main Windows kernel. HVCI contains a code integrity security policy that contains a list of vulnerable drivers that are not allowed to load on the system. As a result, when kprocesshacker.sys tries to load on the system, it is blocked from loading by HVCI, and an analysis of the event logs in the Windows Admin Center shows that the code integrity policy prevented the driver from loading, as this driver was present in the blocklist. This demonstrates how properly configured Secured-core servers can proactively help detect and block threats present on the system.
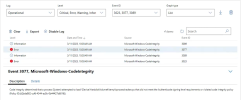
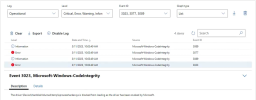
This can also be viewed in the "Advanced hunting" tab within the Microsoft Defender portal, which allows users to explore up to 30 days of events to locate potential threats.
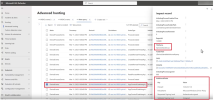
Microsoft Defender for Cloud constantly keeps monitoring your workloads and clusters for active threats on your servers. When the asWarPot.sys on the system, Defender for Cloud blocks the action from taking place. At the same time, based on the communication preferences set forth by the IT admins, an alert is fired indicating that some suspicious activity was taking place in their environments, and that a threat was detected and blocked.

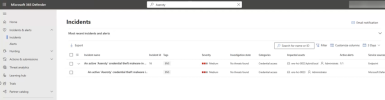
IT admins can log into the Azure Portal and view the security alerts that fired in their server environment, and drill deeper into the specifics of the malware that tried to execute on their systems.
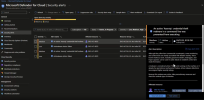
Security response teams within enterprises might be interested in understanding the exact attack chain associated with the malware to set guardrails to prevent similar attacks in the future. When your servers have been onboarded with Defender for Cloud, a Microsoft Defender for Endpoint agent is also installed. The presence of the Defender for Endpoint agents on these machines allows security response teams to dig deeper into the sequence of events that took place leading up to when the malicious event occurred.
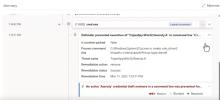
Admins can go the Microsoft Defender portal to view the details associated with the attack, and drill down into exactly what events led to the malicious asWarPot.sys driver attempting to load on the system.
At the end of the day, your workload is only as secure as the foundation it is built on, and Secured-core servers provide a strong and secure foundation to help protect your on-prem infrastructure. It seamlessly integrates with the broader suite of security offerings such as Defender for Cloud to offer even more powerful capabilities such as threat detection, alerting and remediation capabilities.
Since its launch in 2021, we have observed a consistent rise in the adoption of Secured-core servers. In 2022, we have established Secured-core as a prerequisite for all new Azure Stack HCI, version 22H2 solutions built on Gen 3 or newer server-grade silicon platforms. We are also excited to announce that leading manufacturers such as Dell Technologies, HPE, and Lenovo have committed to supporting Secured-core server across all their products based on Gen 3 or newer server-grade silicon platforms for Windows Server 2022 and Windows Server 2025.
Visit the Windows Server catalog or Azure Stack HCI catalog to find out the latest servers and solutions from the breadth of industry leading partners supporting Secured-core server.
Continue reading...
Servers are the backbone of modern businesses, and they store and process vast amounts of sensitive data. As a result, server security is critical to protect against cyberattacks that can cause financial losses, reputational damage, and legal liabilities. In 2021, Microsoft announced the launch of Secured-core servers in partnership with our silicon partners and original equipment manufacturers (OEMs). These servers offer some of the most advanced hardware-based security capabilities that make it harder for adversaries to carry out cyberattacks. In this post, we will provide an example of how the upcoming Windows Server 2025 Secured-core servers seamlessly integrate with the broader suite of Microsoft's security offerings to not just identify but also help block real world attacks.
Bring Your Own Vulnerable Drivers (BYOVD) attack technique
There is an entire class of attacks that rely on an attack technique known as "Bring Your Own Vulnerable Driver" (BYOVD). In these attacks, a malicious adversary with administrative privileges installs a legitimately signed driver with a vulnerability in it on the target system. These drivers have direct access to the internals of the operating system. This vulnerability is then exploited to provide the attacker with the highest level of privileges on the system, which is then used to disable security processes running on the system. We'll now take a couple of vulnerable drivers that have been used in attacks in the past.
kprocesshacker.sys
Process Hacker is a free and open-source malware analysis tool that is used for debugging, malware detection and system monitoring. Process Hacker was used by a ransomware known as DoppelPaymer, which had several high-profile targets such as Foxconn, Kia and Boyce Technologies. DoppelPaymer hijacks ProcessHacker to terminate a list of processes such as those responsible for security, e-mail server, backup and database software to impair defenses. It drops the ProcessHacker executable, its driver and a malicious stager DLL into a subdirectory of %APPDATA%. The driver, known as kprocesshacker.sys, allows it to communicate with the kernel and is used to load the stager DLL via DLL Search Order Hijacking and subsequently, upon receiving a trigger, terminate processes running in the kernel.
asWarPot.sys
AvosLocker is a ransomware group that has targeted victims across multiple critical infrastructure sectors in the United States such as financial services and government facilities sectors. Certain samples of the AvosLocker Ransomware used a legitimate but vulnerable Avast Anti-Rootkit driver known as asWarPot.sys to disable endpoint protection agents and security features on the targeted systems.
Secured-core servers and Microsoft Defender for Cloud in action to help protect against modern threats
Configuring your on-premises servers for hybrid cloud security is made simple with Windows Server 2025. Using the Azure Arc installer wizard included in Windows Server 2025, then onboarding with Microsoft Defender for Cloud will add cloud-based protections to Secured-core servers such as continuous assessment, built-in benchmarks, security recommendations, threat protection capabilities and remediation guidance in case threats have been detected. Here we will discuss how each layer of security works to help protect against threats.
Defense against kprocesshacker.sys using Secured-core servers
Secured-core servers offer a hardware-based security feature known as Hypervisor-protected code integrity (HVCI). HVCI uses Virtualization-based Security (VBS) to run kernel mode code integrity inside a secure, isolated environment instead of the main Windows kernel. HVCI contains a code integrity security policy that contains a list of vulnerable drivers that are not allowed to load on the system. As a result, when kprocesshacker.sys tries to load on the system, it is blocked from loading by HVCI, and an analysis of the event logs in the Windows Admin Center shows that the code integrity policy prevented the driver from loading, as this driver was present in the blocklist. This demonstrates how properly configured Secured-core servers can proactively help detect and block threats present on the system.


This can also be viewed in the "Advanced hunting" tab within the Microsoft Defender portal, which allows users to explore up to 30 days of events to locate potential threats.

Defense against asWarPot.sys using Microsoft Defender for Cloud
Microsoft Defender for Cloud constantly keeps monitoring your workloads and clusters for active threats on your servers. When the asWarPot.sys on the system, Defender for Cloud blocks the action from taking place. At the same time, based on the communication preferences set forth by the IT admins, an alert is fired indicating that some suspicious activity was taking place in their environments, and that a threat was detected and blocked.

IT admins can log into the Azure Portal and view the security alerts that fired in their server environment, and drill deeper into the specifics of the malware that tried to execute on their systems.

Security response teams within enterprises might be interested in understanding the exact attack chain associated with the malware to set guardrails to prevent similar attacks in the future. When your servers have been onboarded with Defender for Cloud, a Microsoft Defender for Endpoint agent is also installed. The presence of the Defender for Endpoint agents on these machines allows security response teams to dig deeper into the sequence of events that took place leading up to when the malicious event occurred.
Admins can go the Microsoft Defender portal to view the details associated with the attack, and drill down into exactly what events led to the malicious asWarPot.sys driver attempting to load on the system.


Protect your on-premises workload with Secured-core servers
At the end of the day, your workload is only as secure as the foundation it is built on, and Secured-core servers provide a strong and secure foundation to help protect your on-prem infrastructure. It seamlessly integrates with the broader suite of security offerings such as Defender for Cloud to offer even more powerful capabilities such as threat detection, alerting and remediation capabilities.
Since its launch in 2021, we have observed a consistent rise in the adoption of Secured-core servers. In 2022, we have established Secured-core as a prerequisite for all new Azure Stack HCI, version 22H2 solutions built on Gen 3 or newer server-grade silicon platforms. We are also excited to announce that leading manufacturers such as Dell Technologies, HPE, and Lenovo have committed to supporting Secured-core server across all their products based on Gen 3 or newer server-grade silicon platforms for Windows Server 2022 and Windows Server 2025.
Visit the Windows Server catalog or Azure Stack HCI catalog to find out the latest servers and solutions from the breadth of industry leading partners supporting Secured-core server.
Additional resources
- What is Secured-core server for Windows Server
- Protect your infrastructure with Secured-core server
- Microsoft brings advanced hardware security to Server and Edge with Secured-core
- Try Windows Server 2025 now in preview
- Learn about the upcoming Windows Server 2025
Continue reading...