- Staff
- #1
MS Server
Staff member
- May 17, 2015
This is a post from Nir Ben Zvi, Principal PM Manager, Microsoft
Cybersecurity has hit the mainstream. You would be hard pressed to find someone who doesn’t know about a company that has been breached and dragged across the news. Security veterans might say that this is just the tip of the iceberg but you have to admit – it’s a very large tip.
The actors and their motives have changed - A few years back, the Microsoft Trustworthy Computing group published an internal position paper that predicted a shift in the security attack profile and sophistication of actors and called out the need to develop technologies and solutions to address Advanced Persistent Threats (APT) and insider attacks. This prompted major efforts across many areas in the company, ranging from the Microsoft Azure public cloud to Windows 10 and the various Server teams.
In parallel, the ongoing landscape shifts have a profound effect on security: virtualization, the large-scale cloud computing model, and the public cloud, which introduces a trust boundary between the tenant and the service provider. The security and operations of the Microsoft Azure cloud is an ongoing source of great innovations that we can draw from to help deliver security that addresses this new world.
This post is intended to provide you with insight into our efforts to improve the security in datacenters, private cloud and hosting environment.
At Ignite 2015 we have a set of sessions that will go into the details of our investments and roadmap. First and foremost: “Platform Vision & Strategy (5 of 7): Security and Assurance Overview (May. 5, 3:15pm-4:30pm)” Security and Assurance 5 minute overview by Microsoft's Technical Fellow, Anders Vinberg
Principles for security and assurance solutions
Throughout our work in the security and assurance area we established a few key guiding principles
Before moving on, a note about Compliance and Security/Assurance. Many of you reading this blog work in companies that need to adhere to one or more sets of compliance regulations. While being compliant does not mean that you’re guaranteed to be secure, adopting and implementing breach resistant security mechanisms may greatly contribute to your compliance stance.
Datacenter and cloud security
The security experts tell us that most of the recent attacks use compromised administrator credentials. We know that social engineering works, people can be fooled; and bribery works; and we have insider attacks. But there are things we can do if we adopt an “Assume Breach” mindset as we approach security controls.
Adopting this new mindset requires us to look at what a breached system or compromised account mean to the environment, how we can limit the breach impact, make it detectable and have the ability to respond. This approach works well in combination with the traditional security stance of preventing attacks and keeping the bad guys out.
Our current initiatives fall in three buckets:
The virtualization landscape shift has a profound effect on security as it introduces a new trust boundary between the tenant and the datacenter admin/service provider (hoster)
To put it plainly, if a datacenter administrator account is compromised, then all the virtual machines (Workloads) running in that datacenter are accessible to the attacker who is then able to both access sensitive information and inject malicious executables. This is true for anyone that has administrator access to the storage, network, backup and physical machines on the fabric as well as the fabric managers.
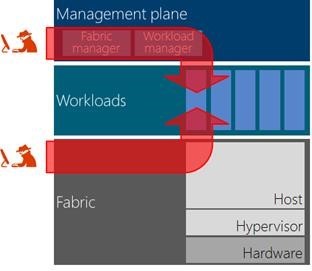
To protect the workload from fabric attacks, we have introduced something we call a “trust plane”. This is analogous to the management plane that is used to manage the workloads and the fabric. The trust plane is separate, it is isolated from the fabric and the management plane, and administrators do not have access to the trust plane.
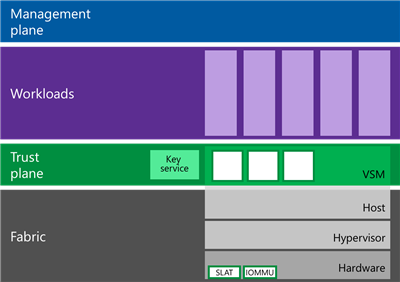
At the heart of the trust plane is a new technology called: “Virtual Secure Mode” (VSM): we use the hypervisor and the hardware to create a space that is entirely separate from the rest of the system. Inside VSM there are only specific binaries and information that are not accessible or controlled by the administrator. No software can be introduced, nobody can get admin privileges and it is not connected to the network. In VSM, we can execute and store security critical operations like secure key management and protecting the integrity of the system.
With this Trust Plane, we can now use cryptographic technology to protect virtual machines and their data files and databases.
In Windows Server 2016 we are introducing “Shielded Virtual Machines” (Shielded VM) to achieve isolation between the fabric/host and the Virtual Machine. This capability will be available for on-premises private clouds and service providers (hosters).
While Shielded VMs look just like any other Virtual Machine to the fabric management tools, they are:
This allows you to achieve a high level of assurance for all the workloads that you’re virtualizing and in addition, enable you to virtualize sensitive workloads such as domain controllers, which were traditionally kept on physical machines.
It’s a simple concept, but we also took a lot of care to make sure we have a practical solution that does not require a re-architecture of the fabric; so we also made Shielded VMs integrate well with the current operational model of the entire lifecycle of a VM: Shielded VMs can be paused and stored and restarted and migrated, and there is disaster recovery and backup and many other things.
Ignite 2015 session: Harden the Fabric: Protecting Tenant Secrets in Hyper-V (Wednesday, May 6th 03:15PM - 04:30PM)
Privileged Access Management
Workloads are also exposed to other threats through administrator account compromise.
When analyzing the numerous breaches over the past few years, one quickly concludes that no matter what method was used to breach the environment, the attackers proceed to compromising administrator credentials so that they can integrate, control and hide inside the environment.
Privileged Access Management is another aspect of the “Assume Breach” mindset: in addition to working to prevent breach, we also contain the potential damage of a breach.
There are many benefits and aspects of Privileged Access Management but from an “Assume Breach” perspective”. Privileged Access Management enables key capabilities including:
We have been using JIT and JEA technologies in our Azure and Office 365 cloud operations and are now very excited to introduce these as public solutions targeted at protecting your existing environments.
We are releasing “Just In Time” capabilities (and much more) in the upcoming Microsoft Identity Manager (MIM) 2016 which is already available in public preview (see AD blog).
We have also published the xJEA PowerShell module for “Just Enough Administration” and will soon follow up with an update integrated into the Windows Management Framework (see JEA blog).
Both the JIT and JEA solutions focus on ease of adoption so that you can plug these into your existing infrastructure to help you control and monitor privilege access.
Ignite 2015 sessions:
And this brings us to the detection and forensics. We know that the attackers are clever, and they learn and adapt. So detection is essential, and we can now use the power of the cloud to do that. We can collect information from many sources, fabrics and VMs in both private and public clouds, as well as anti-malware systems, our cyber-crime unit, industry partnerships, government sources and others.
This provides vast amounts of data, and we can put all this data in the cloud and use Big Data and Machine Learning technologies for analysis.
Again, we have been using these techniques internally for some time, but now we’ll make it available as services to our customers. This is a rapidly evolving area, we continually learn and this is one of the advantages of delivering this functionality as a service: as we learn, we can improve the service on a continual basis.
There are two very exciting offerings that we are delivering in this area in the immediate future:
The “Microsoft Advanced Threat Analytics” is an on-premises product that use Active Directory network traffic and SIEM data to discover and alert on potential threats. Since it uses targeted Active Directory data, Microsoft ATA is able to achieve high accuracy in identifying and alerting on malicious behavior as it happens and map the impact potential impact of the attacker.
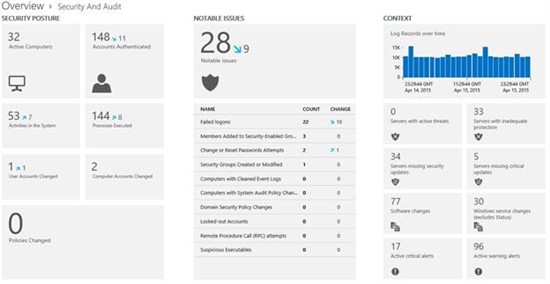
The Microsoft Operations Management Suite (OMS) Security and Audit solution processes security logs and firewall events from on-premises and cloud environments to analyze and detect malicious behavior. Using this Security and Audit solution, an IT Pro is able to review suspicious behavior and decide whether further investigation is required by a security analyst. If so, the analyst can then use the query capabilities of the tool for a more thorough investigation.
Ignite 2015 sessions:
The way a breach spreads is that attackers inside your network use known vulnerabilities to take control over servers and then harvest administrator credentials in order to spread across your environment.
To help you with the fundamentals, we have built “system update assessment” to discover which systems need to be patched and “malware assessment” into the Microsoft Operations Management Suite (OMS) so that you can discover and take action on patching and securing servers in your environment. We have also worked to include Windows Server Antimalware, which is enabled by default, in Windows Server 2016.
In summary
To address the evolving security threat landscape and shifts driven by cloud computing, we have combined the “Assume Breach” mindset with the experience of running a public cloud to deliver a set of solutions and technologies to provide protection for existing environments, while keeping in mind consistency across clouds.
These include protecting your virtual machines, privileged access management and detection and analysis services.
These solutions focus not only on security but also on being practical and easy to adopt into your current environment.
Security is an ongoing journey and we are committed to continuing our efforts to help customers protect their environments.

Continue reading...
Cybersecurity has hit the mainstream. You would be hard pressed to find someone who doesn’t know about a company that has been breached and dragged across the news. Security veterans might say that this is just the tip of the iceberg but you have to admit – it’s a very large tip.
The actors and their motives have changed - A few years back, the Microsoft Trustworthy Computing group published an internal position paper that predicted a shift in the security attack profile and sophistication of actors and called out the need to develop technologies and solutions to address Advanced Persistent Threats (APT) and insider attacks. This prompted major efforts across many areas in the company, ranging from the Microsoft Azure public cloud to Windows 10 and the various Server teams.
In parallel, the ongoing landscape shifts have a profound effect on security: virtualization, the large-scale cloud computing model, and the public cloud, which introduces a trust boundary between the tenant and the service provider. The security and operations of the Microsoft Azure cloud is an ongoing source of great innovations that we can draw from to help deliver security that addresses this new world.
This post is intended to provide you with insight into our efforts to improve the security in datacenters, private cloud and hosting environment.
At Ignite 2015 we have a set of sessions that will go into the details of our investments and roadmap. First and foremost: “Platform Vision & Strategy (5 of 7): Security and Assurance Overview (May. 5, 3:15pm-4:30pm)” Security and Assurance 5 minute overview by Microsoft's Technical Fellow, Anders Vinberg
Principles for security and assurance solutions
Throughout our work in the security and assurance area we established a few key guiding principles
- Assume breach, analyze the environment to determine how an attack may propagate and make changes to contain any compromise.
- Embrace the cloud landscape shifts and cloud consistency to enable security in large scale virtualized environments.
- Protect existing environments without requiring major upgrades and re-architecture of your datacenter or hosting infrastructure.
Before moving on, a note about Compliance and Security/Assurance. Many of you reading this blog work in companies that need to adhere to one or more sets of compliance regulations. While being compliant does not mean that you’re guaranteed to be secure, adopting and implementing breach resistant security mechanisms may greatly contribute to your compliance stance.
Datacenter and cloud security
The security experts tell us that most of the recent attacks use compromised administrator credentials. We know that social engineering works, people can be fooled; and bribery works; and we have insider attacks. But there are things we can do if we adopt an “Assume Breach” mindset as we approach security controls.
Adopting this new mindset requires us to look at what a breached system or compromised account mean to the environment, how we can limit the breach impact, make it detectable and have the ability to respond. This approach works well in combination with the traditional security stance of preventing attacks and keeping the bad guys out.
Our current initiatives fall in three buckets:
- Protecting Virtual Machines (Workloads) from attacks through the private cloud or service provider fabric
- Privileged Access Management to address threats that result from compromised administrator credentials
- Threat and malicious behavior detection
The virtualization landscape shift has a profound effect on security as it introduces a new trust boundary between the tenant and the datacenter admin/service provider (hoster)
To put it plainly, if a datacenter administrator account is compromised, then all the virtual machines (Workloads) running in that datacenter are accessible to the attacker who is then able to both access sensitive information and inject malicious executables. This is true for anyone that has administrator access to the storage, network, backup and physical machines on the fabric as well as the fabric managers.

To protect the workload from fabric attacks, we have introduced something we call a “trust plane”. This is analogous to the management plane that is used to manage the workloads and the fabric. The trust plane is separate, it is isolated from the fabric and the management plane, and administrators do not have access to the trust plane.
At the heart of the trust plane is a new technology called: “Virtual Secure Mode” (VSM): we use the hypervisor and the hardware to create a space that is entirely separate from the rest of the system. Inside VSM there are only specific binaries and information that are not accessible or controlled by the administrator. No software can be introduced, nobody can get admin privileges and it is not connected to the network. In VSM, we can execute and store security critical operations like secure key management and protecting the integrity of the system.

With this Trust Plane, we can now use cryptographic technology to protect virtual machines and their data files and databases.
In Windows Server 2016 we are introducing “Shielded Virtual Machines” (Shielded VM) to achieve isolation between the fabric/host and the Virtual Machine. This capability will be available for on-premises private clouds and service providers (hosters).
While Shielded VMs look just like any other Virtual Machine to the fabric management tools, they are:
- Encrypted (using BitLocker) on storage and on the wire
- Can only be executed on hosts that are appropriately configured (verified by remote attestation)
- Not accessible to fabric, storage, network administrators and are hardened (based on configuration) against malicious host administrator access.
This allows you to achieve a high level of assurance for all the workloads that you’re virtualizing and in addition, enable you to virtualize sensitive workloads such as domain controllers, which were traditionally kept on physical machines.
It’s a simple concept, but we also took a lot of care to make sure we have a practical solution that does not require a re-architecture of the fabric; so we also made Shielded VMs integrate well with the current operational model of the entire lifecycle of a VM: Shielded VMs can be paused and stored and restarted and migrated, and there is disaster recovery and backup and many other things.
Ignite 2015 session: Harden the Fabric: Protecting Tenant Secrets in Hyper-V (Wednesday, May 6th 03:15PM - 04:30PM)
Privileged Access Management
Workloads are also exposed to other threats through administrator account compromise.
When analyzing the numerous breaches over the past few years, one quickly concludes that no matter what method was used to breach the environment, the attackers proceed to compromising administrator credentials so that they can integrate, control and hide inside the environment.
Privileged Access Management is another aspect of the “Assume Breach” mindset: in addition to working to prevent breach, we also contain the potential damage of a breach.
There are many benefits and aspects of Privileged Access Management but from an “Assume Breach” perspective”. Privileged Access Management enables key capabilities including:
- By default – no one has privileged access
- When someone needs to perform administrative actions, they request to be an administrator (“Check out”) for a set period of time by going through an approval process that can range from automatic, to multi-factor authentication and manual approval. We use the term “Just In Time” administration (JIT) to describe this functionality.
- When granted administrative privilege, the user can only perform certain tasks, and they are not full administrators on the server they are managing. We use the term “Just Enough Administration” (JEA) to describe this functionality.
- Everything is logged from the request workflow to the administrative operations performed on the servers, so that it is easier to monitor and detect malicious behavior.
We have been using JIT and JEA technologies in our Azure and Office 365 cloud operations and are now very excited to introduce these as public solutions targeted at protecting your existing environments.
We are releasing “Just In Time” capabilities (and much more) in the upcoming Microsoft Identity Manager (MIM) 2016 which is already available in public preview (see AD blog).
We have also published the xJEA PowerShell module for “Just Enough Administration” and will soon follow up with an update integrated into the Windows Management Framework (see JEA blog).
Both the JIT and JEA solutions focus on ease of adoption so that you can plug these into your existing infrastructure to help you control and monitor privilege access.
Ignite 2015 sessions:
- Protecting Windows and Microsoft Azure Active Directory with Privileged Access Management (Thursday, May 7th, 5:00 PM – 6:15 PM)
- JEA: A PowerShell Toolkit to Secure a Post-Snowden World (May. 7, 9:00am-10:15am)
And this brings us to the detection and forensics. We know that the attackers are clever, and they learn and adapt. So detection is essential, and we can now use the power of the cloud to do that. We can collect information from many sources, fabrics and VMs in both private and public clouds, as well as anti-malware systems, our cyber-crime unit, industry partnerships, government sources and others.
This provides vast amounts of data, and we can put all this data in the cloud and use Big Data and Machine Learning technologies for analysis.
Again, we have been using these techniques internally for some time, but now we’ll make it available as services to our customers. This is a rapidly evolving area, we continually learn and this is one of the advantages of delivering this functionality as a service: as we learn, we can improve the service on a continual basis.
There are two very exciting offerings that we are delivering in this area in the immediate future:
The “Microsoft Advanced Threat Analytics” is an on-premises product that use Active Directory network traffic and SIEM data to discover and alert on potential threats. Since it uses targeted Active Directory data, Microsoft ATA is able to achieve high accuracy in identifying and alerting on malicious behavior as it happens and map the impact potential impact of the attacker.
The Microsoft Operations Management Suite (OMS) Security and Audit solution processes security logs and firewall events from on-premises and cloud environments to analyze and detect malicious behavior. Using this Security and Audit solution, an IT Pro is able to review suspicious behavior and decide whether further investigation is required by a security analyst. If so, the analyst can then use the query capabilities of the tool for a more thorough investigation.

Ignite 2015 sessions:
- Security Threat Analysis using Microsoft Azure Operational Insights (May. 7, 1:30pm-2:45pm)
- How to Protect Your Corporate Resources from Advanced Attacks (Tuesday, May 5th, 10:45 AM – 12:00 PM)
The way a breach spreads is that attackers inside your network use known vulnerabilities to take control over servers and then harvest administrator credentials in order to spread across your environment.
To help you with the fundamentals, we have built “system update assessment” to discover which systems need to be patched and “malware assessment” into the Microsoft Operations Management Suite (OMS) so that you can discover and take action on patching and securing servers in your environment. We have also worked to include Windows Server Antimalware, which is enabled by default, in Windows Server 2016.
In summary
To address the evolving security threat landscape and shifts driven by cloud computing, we have combined the “Assume Breach” mindset with the experience of running a public cloud to deliver a set of solutions and technologies to provide protection for existing environments, while keeping in mind consistency across clouds.
These include protecting your virtual machines, privileged access management and detection and analysis services.
These solutions focus not only on security but also on being practical and easy to adopt into your current environment.
Security is an ongoing journey and we are committed to continuing our efforts to help customers protect their environments.

Continue reading...