Server Man
Well-Known Member
- May 17, 2015
~ Somaning Turwale | Support Escalation Engineer
 This post covers managing untrusted hosts in System Center 2012 R2 Virtual Machine Manager (VMM 2012 R2). Adding Hyper-V hosts or Hyper-V host clusters in an untrusted Active Directory domain as managed Hyper-V hosts in Virtual Machine Manager (VMM) is documented here: https://technet.microsoft.com/en-in/library/gg610609.aspx.
This post covers managing untrusted hosts in System Center 2012 R2 Virtual Machine Manager (VMM 2012 R2). Adding Hyper-V hosts or Hyper-V host clusters in an untrusted Active Directory domain as managed Hyper-V hosts in Virtual Machine Manager (VMM) is documented here: https://technet.microsoft.com/en-in/library/gg610609.aspx.
NOTE Be aware that during the agent installation, VMM generates a certificate that is used to secure communications with the host. When VMM adds the host, the certificate is automatically imported into the VMM server’s trusted certificate store.
How to update the Untrusted VMM agents
When an Update Rollup (UR) is installed on VMM server, all managed hosts will show a Needs Attention status, however when you try to update the agents on any untrusted host, the below error message is displayed:
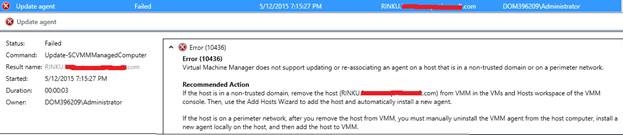
Error (10436)
Virtual Machine Manager does not support updating or re-associating an agent on a host that is in a non-trusted domain or on a perimeter network.
Recommended Action
If the host is in a non-trusted domain, remove the host (RINKU.Contoso.com) from VMM in the VMs and Hosts workspace of the VMM console. Then, use the Add Hosts Wizard to add the host and automatically install a new agent.
If the host is on a perimeter network, after you remove the host from VMM, you must manually uninstall the VMM agent from the host computer, install a new agent locally on the host, and then add the host to VMM.
As stated in the error message, the host or cluster can be removed and re-added, however this approach will cause an issue if service templates are deployed on these untrusted hosts.
The following procedure should be used when updating the VMM agent on untrusted hosts:
1. Take a full backup of the System Center 2012 R2 Virtual Machine Manager database.
2. Log in to the untrusted host and uninstall the VMM agent using Add/Remove Programs.
3. Copy the latest VMM agent installation files from C:\Program Files\Microsoft System Center 2012 R2\Virtual Machine Manager\agents\amd64 on the VMM server to a temporary location on the host. In my case I am upgrading to Update Rollup 6 so I copied the 3.2.8002.0version to the host.
4. Open an elevated Command Prompt (Run as Administrator) on the host.
5. From the Command Prompt, change the path to the location where you copied the installation files (e.g. CD C:\temp\3.2.8002.0).
6. From the Command Prompt, run the command below:
VMMagent.msi NONTRUSTEDMACHINE=1 ENCRYPTIONKEY=********** CREDENTIALEXPORTDIRECTORY=\\localhost\admin$ WSMANPORT=5986 BITSPORT=443 REBOOT=ReallySuppress CURRENTDIRECTORY=C:\Windows\system32 CLIENTUILEVEL=3 MSICLIENTUSESEXTERNALUI=1 CLIENTPROCESSID=6836
Note that the command above is one line and may wrap on your display.
7. The VMM Agent installation wizard will open. Click Next to continue.
8. The wizard will prompt for the encryption key. Retype the encryption key and confirm the information.
9. Follow the wizard to install the agent.
10. Once the agent is installed successfully, go to Computer Management\Local users and Groups\Users.
11. You will see the local user created by the VMM agent installation with a name similar to SCVMM as shown in the screen shot below:
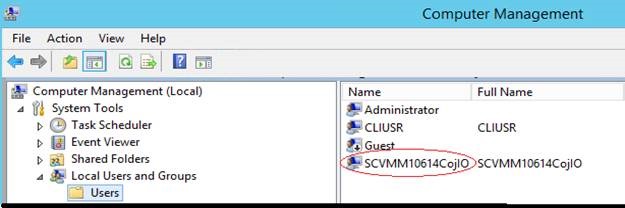
12. Go to the Properties of the local user and on the Member of tab add the user to the “Virtual Machine Manager Servers” group.
13. Click Start, then Run, then run certlm.msc
14. Expand the Personal store.
15. Locate the certificate with a friendly name starting with SCVMM_CERTIFICATE_KEY_CONTAINER.
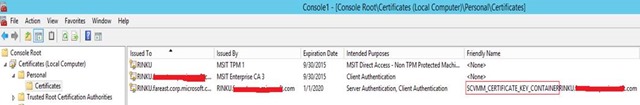
16. Right-click on that certificate and select All Tasks and then choose Export… Follow the wizard's prompts and choose the default options.
17. Copy the exported certificate to the VMM server.
18. On the VMM server, repeat steps 13 through 16.
19. Expand Trusted People.
20. Delete the existing certificate for the untrusted host.
21. Right-click on Trusted People, select All Tasks and then Import.
22. Browse to the path where you copied the certificate on step 21.
23. Once the import is successful, open the VMM console and refresh the host.
24. The host should now show a status of OK.
Somaning Turwale | Support Escalation Engineer | Microsoft GBS Management and Security Division
Get the latest System Center news on Facebook and Twitter:


System Center All Up: http://blogs.technet.com/b/systemcenter/
Configuration Manager Support Team blog: http://blogs.technet.com/configurationmgr/
Data Protection Manager Team blog: http://blogs.technet.com/dpm/
Orchestrator Support Team blog: http://blogs.technet.com/b/orchestrator/
Operations Manager Team blog: http://blogs.technet.com/momteam/
Service Manager Team blog: http://blogs.technet.com/b/servicemanager
Virtual Machine Manager Team blog: http://blogs.technet.com/scvmm
Microsoft Intune: http://blogs.technet.com/b/microsoftintune/
WSUS Support Team blog: http://blogs.technet.com/sus/
The RMS blog: http://blogs.technet.com/b/rms/
App-V Team blog: http://blogs.technet.com/appv/
MED-V Team blog: http://blogs.technet.com/medv/
Server App-V Team blog: http://blogs.technet.com/b/serverappv
The Surface Team blog: http://blogs.technet.com/b/surface/
The Application Proxy blog: http://blogs.technet.com/b/applicationproxyblog/
The Forefront Endpoint Protection blog : http://blogs.technet.com/b/clientsecurity/
The Forefront Identity Manager blog : http://blogs.msdn.com/b/ms-identity-support/
The Forefront TMG blog: http://blogs.technet.com/b/isablog/
The Forefront UAG blog: http://blogs.technet.com/b/edgeaccessblog/

Continue reading...

NOTE Be aware that during the agent installation, VMM generates a certificate that is used to secure communications with the host. When VMM adds the host, the certificate is automatically imported into the VMM server’s trusted certificate store.
How to update the Untrusted VMM agents
When an Update Rollup (UR) is installed on VMM server, all managed hosts will show a Needs Attention status, however when you try to update the agents on any untrusted host, the below error message is displayed:

Error (10436)
Virtual Machine Manager does not support updating or re-associating an agent on a host that is in a non-trusted domain or on a perimeter network.
Recommended Action
If the host is in a non-trusted domain, remove the host (RINKU.Contoso.com) from VMM in the VMs and Hosts workspace of the VMM console. Then, use the Add Hosts Wizard to add the host and automatically install a new agent.
If the host is on a perimeter network, after you remove the host from VMM, you must manually uninstall the VMM agent from the host computer, install a new agent locally on the host, and then add the host to VMM.
As stated in the error message, the host or cluster can be removed and re-added, however this approach will cause an issue if service templates are deployed on these untrusted hosts.
The following procedure should be used when updating the VMM agent on untrusted hosts:
1. Take a full backup of the System Center 2012 R2 Virtual Machine Manager database.
2. Log in to the untrusted host and uninstall the VMM agent using Add/Remove Programs.
3. Copy the latest VMM agent installation files from C:\Program Files\Microsoft System Center 2012 R2\Virtual Machine Manager\agents\amd64 on the VMM server to a temporary location on the host. In my case I am upgrading to Update Rollup 6 so I copied the 3.2.8002.0version to the host.
4. Open an elevated Command Prompt (Run as Administrator) on the host.
5. From the Command Prompt, change the path to the location where you copied the installation files (e.g. CD C:\temp\3.2.8002.0).
6. From the Command Prompt, run the command below:
VMMagent.msi NONTRUSTEDMACHINE=1 ENCRYPTIONKEY=********** CREDENTIALEXPORTDIRECTORY=\\localhost\admin$ WSMANPORT=5986 BITSPORT=443 REBOOT=ReallySuppress CURRENTDIRECTORY=C:\Windows\system32 CLIENTUILEVEL=3 MSICLIENTUSESEXTERNALUI=1 CLIENTPROCESSID=6836
Note that the command above is one line and may wrap on your display.
7. The VMM Agent installation wizard will open. Click Next to continue.
8. The wizard will prompt for the encryption key. Retype the encryption key and confirm the information.
9. Follow the wizard to install the agent.
10. Once the agent is installed successfully, go to Computer Management\Local users and Groups\Users.
11. You will see the local user created by the VMM agent installation with a name similar to SCVMM as shown in the screen shot below:

12. Go to the Properties of the local user and on the Member of tab add the user to the “Virtual Machine Manager Servers” group.
13. Click Start, then Run, then run certlm.msc
14. Expand the Personal store.
15. Locate the certificate with a friendly name starting with SCVMM_CERTIFICATE_KEY_CONTAINER.

16. Right-click on that certificate and select All Tasks and then choose Export… Follow the wizard's prompts and choose the default options.
17. Copy the exported certificate to the VMM server.
18. On the VMM server, repeat steps 13 through 16.
19. Expand Trusted People.
20. Delete the existing certificate for the untrusted host.
21. Right-click on Trusted People, select All Tasks and then Import.
22. Browse to the path where you copied the certificate on step 21.
23. Once the import is successful, open the VMM console and refresh the host.
24. The host should now show a status of OK.
Somaning Turwale | Support Escalation Engineer | Microsoft GBS Management and Security Division
Get the latest System Center news on Facebook and Twitter:


System Center All Up: http://blogs.technet.com/b/systemcenter/
Configuration Manager Support Team blog: http://blogs.technet.com/configurationmgr/
Data Protection Manager Team blog: http://blogs.technet.com/dpm/
Orchestrator Support Team blog: http://blogs.technet.com/b/orchestrator/
Operations Manager Team blog: http://blogs.technet.com/momteam/
Service Manager Team blog: http://blogs.technet.com/b/servicemanager
Virtual Machine Manager Team blog: http://blogs.technet.com/scvmm
Microsoft Intune: http://blogs.technet.com/b/microsoftintune/
WSUS Support Team blog: http://blogs.technet.com/sus/
The RMS blog: http://blogs.technet.com/b/rms/
App-V Team blog: http://blogs.technet.com/appv/
MED-V Team blog: http://blogs.technet.com/medv/
Server App-V Team blog: http://blogs.technet.com/b/serverappv
The Surface Team blog: http://blogs.technet.com/b/surface/
The Application Proxy blog: http://blogs.technet.com/b/applicationproxyblog/
The Forefront Endpoint Protection blog : http://blogs.technet.com/b/clientsecurity/
The Forefront Identity Manager blog : http://blogs.msdn.com/b/ms-identity-support/
The Forefront TMG blog: http://blogs.technet.com/b/isablog/
The Forefront UAG blog: http://blogs.technet.com/b/edgeaccessblog/

Continue reading...