Server Man
Well-Known Member
- May 17, 2015

- Windows 10

- IE 11
Azure Advanced Threat Protection (Azure ATP) is a cloud service that helps protect your enterprise hybrid environments from multiple types of advanced targeted cyber-attacks and insider threats, leveraging machine learning analytics to determine suspicious user behavior. In the six months since its release, Azure Advanced Threat Protection (Azure ATP) now protects millions of users at organizations worldwide and is continuously updated with new detections.
New Detections & Alerts
As new threats and attack methods are discovered in the wild, Azure ATP leverages the cloud to push out new detection capabilities to help secure your organization in a constantly changing security landscape.
Attackers with domain admin rights can compromise the KRBTGT account. Using the KRBTGT account, they can create a Kerberos ticket granting ticket (TGT) that provides authorization to any resource. This fake TGT is called a "Golden Ticket" and allows attackers to achieve persistency in the network.
In this detection, an alert is triggered when a Kerberos ticket granting ticket is used by a nonexistent account.
A domain controller shadow (DCShadow) attack is an attack designed to change directory objects using malicious replication. This attack can be performed from any machine by creating a rogue domain controller using a replication process.
In this detection, an alert is triggered when a machine in the network is trying to register as a rogue domain controller.
Many organizations let users login remotely into sensitive on-premises resources using a secure VPN connection. Attackers who have compromised an identity can use that user’s VPN credentials to log-in to corporate-assets. Azure ATP analyzes user VPN connectivity behavior and can alert upon suspicious VPN activity – such as logging in from an unfamiliar location or using an unfamiliar device.
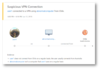 Additionally, we have improved the existing security alerts, making them easier to understand and investigate by SecOps. A feature of the improved alerts is the evidence section, which provides detailed information about the alert, explaining what happened and increasing your confidence in the alert.
Additionally, we have improved the existing security alerts, making them easier to understand and investigate by SecOps. A feature of the improved alerts is the evidence section, which provides detailed information about the alert, explaining what happened and increasing your confidence in the alert.
Easy to deploy
Azure ATP is easy to deploy across large and small organizations – a recent customer deployed over 800 Azure ATP sensors in less than 2 days to hundreds of cities across the globe. We have also updated the service to allow you the option to set Azure ATP sensors to update at a later time, each time Azure ATP updates. You can now set some of your Azure ATP sensors to Delayed update so that they will update 24 hours after the Azure ATP cloud service updates.
Azure ATP now also supports organizations with multiple forests which gives you the ability to monitor activity and profile users across forests to further improve operations. Azure ATP has also been updated to notify you if your domain controller’s existing Advanced Audit Policies are not correctly configured to provide maximum Azure ATP service coverage for your organization.
New Integrations Planned: Azure Active Directory Identity Protection + Azure ATP
Azure ATP is being integrated with Azure Active Directory Identity Protection (Azure AD IP), and this functionality is expected to be available for Preview later this year. With this integration, Microsoft will deliver a unified identity investigation experience across on-prem and cloud activities. The integration allows SecOps investigations of at-risk users across your organization through a single pane of glass. SecOps analysts will be able to see a user’s Risk Score as calculated by Azure AD Identity Protection along with the new Azure ATP Investigation Priority which highlights the most important users the security team needs to triage.
Get Started Today
Leveraging the scale and intelligence of the Microsoft Intelligence Security Graph, Azure ATP is part of Microsoft 365’s Enterprise Mobility + Security E5 suite.
Continue reading...
New Detections & Alerts
As new threats and attack methods are discovered in the wild, Azure ATP leverages the cloud to push out new detection capabilities to help secure your organization in a constantly changing security landscape.
Attackers with domain admin rights can compromise the KRBTGT account. Using the KRBTGT account, they can create a Kerberos ticket granting ticket (TGT) that provides authorization to any resource. This fake TGT is called a "Golden Ticket" and allows attackers to achieve persistency in the network.
In this detection, an alert is triggered when a Kerberos ticket granting ticket is used by a nonexistent account.
A domain controller shadow (DCShadow) attack is an attack designed to change directory objects using malicious replication. This attack can be performed from any machine by creating a rogue domain controller using a replication process.
In this detection, an alert is triggered when a machine in the network is trying to register as a rogue domain controller.
Many organizations let users login remotely into sensitive on-premises resources using a secure VPN connection. Attackers who have compromised an identity can use that user’s VPN credentials to log-in to corporate-assets. Azure ATP analyzes user VPN connectivity behavior and can alert upon suspicious VPN activity – such as logging in from an unfamiliar location or using an unfamiliar device.
 Additionally, we have improved the existing security alerts, making them easier to understand and investigate by SecOps. A feature of the improved alerts is the evidence section, which provides detailed information about the alert, explaining what happened and increasing your confidence in the alert.
Additionally, we have improved the existing security alerts, making them easier to understand and investigate by SecOps. A feature of the improved alerts is the evidence section, which provides detailed information about the alert, explaining what happened and increasing your confidence in the alert.Easy to deploy
Azure ATP is easy to deploy across large and small organizations – a recent customer deployed over 800 Azure ATP sensors in less than 2 days to hundreds of cities across the globe. We have also updated the service to allow you the option to set Azure ATP sensors to update at a later time, each time Azure ATP updates. You can now set some of your Azure ATP sensors to Delayed update so that they will update 24 hours after the Azure ATP cloud service updates.
Azure ATP now also supports organizations with multiple forests which gives you the ability to monitor activity and profile users across forests to further improve operations. Azure ATP has also been updated to notify you if your domain controller’s existing Advanced Audit Policies are not correctly configured to provide maximum Azure ATP service coverage for your organization.
New Integrations Planned: Azure Active Directory Identity Protection + Azure ATP
Azure ATP is being integrated with Azure Active Directory Identity Protection (Azure AD IP), and this functionality is expected to be available for Preview later this year. With this integration, Microsoft will deliver a unified identity investigation experience across on-prem and cloud activities. The integration allows SecOps investigations of at-risk users across your organization through a single pane of glass. SecOps analysts will be able to see a user’s Risk Score as calculated by Azure AD Identity Protection along with the new Azure ATP Investigation Priority which highlights the most important users the security team needs to triage.

Get Started Today
Leveraging the scale and intelligence of the Microsoft Intelligence Security Graph, Azure ATP is part of Microsoft 365’s Enterprise Mobility + Security E5 suite.
- Learn more about Azure ATP here: Technical Documentation
- Start a trial from our Azure Advanced Threat Protection Product Page
- Join the Azure ATP community: Technical Community or on Yammer
Continue reading...