Server Man
Well-Known Member
- May 17, 2015

- Windows 10

- Chrome 69.0.3497.100
This post is authored by Tal Maor, Security Researcher, Azure ATP.
DCShadow attack, discovered by Vincent LE TOUX and Benjamin Delpy, was presented at Microsoft BlueHat-IL in January. After the release of Azure Advanced Threat Protection (Azure ATP), and as part of our ongoing research for developing new detections, we were able to deploy this detection to the Azure ATP sensor.
A domain controller shadow DCShadow attack is an attack designed to change directory objects using malicious replication. During this attack, DCShadow impersonates a replicator Domain Controller using administrative rights and starts a replication process, so that changes made on one Domain Controller are synchronized with other Domain Controllers.
Given the necessary permissions, attackers attempt to initiate a malicious replication request, allowing them to change Active Directory objects on a genuine Domain Controller to grant persistence in the domain.
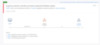
Any suspicious Domain Controller registration or suspicious replication requests against an Azure ATP-protected Domain Controller, the Suspicious Activity detection signals an alert in the Azure ATP timeline, as shown below.
Get Started Today
Leveraging the scale and intelligence of the Microsoft Intelligence Security Graph, Azure ATP is part of Microsoft 365’s Enterprise Mobility + Security E5 suite.
Continue reading...
DCShadow attack, discovered by Vincent LE TOUX and Benjamin Delpy, was presented at Microsoft BlueHat-IL in January. After the release of Azure Advanced Threat Protection (Azure ATP), and as part of our ongoing research for developing new detections, we were able to deploy this detection to the Azure ATP sensor.
A domain controller shadow DCShadow attack is an attack designed to change directory objects using malicious replication. During this attack, DCShadow impersonates a replicator Domain Controller using administrative rights and starts a replication process, so that changes made on one Domain Controller are synchronized with other Domain Controllers.
Given the necessary permissions, attackers attempt to initiate a malicious replication request, allowing them to change Active Directory objects on a genuine Domain Controller to grant persistence in the domain.
Any suspicious Domain Controller registration or suspicious replication requests against an Azure ATP-protected Domain Controller, the Suspicious Activity detection signals an alert in the Azure ATP timeline, as shown below.
Get Started Today
Leveraging the scale and intelligence of the Microsoft Intelligence Security Graph, Azure ATP is part of Microsoft 365’s Enterprise Mobility + Security E5 suite.
- Learn more about Azure ATP here: Technical Documentation
- Start a trial from our Azure Advanced Threat Protection Product Page
- Join the Azure ATP community: Technical Community or on Yammer
Continue reading...