Server Man
Well-Known Member
- May 17, 2015

- Windows 7

- Firefox 62.0
Hello everyone, Jonathan Warnken here, and I am a Premier Field Engineer (PFE) for Microsoft. I primarily support Configuration Manager and I have been getting a lot of questions recently on how to collect custom information and include it in the device inventory within Configuration Manager. I wanted to share one way to accomplish this that demonstrates some of the great ways to extend the built-in features. For this post, I am going to show how to capture the information about local machine certificates. I do want to take a moment to thank MVP Sherry Kissinger for this post with the base powershell script used to collect the certificate information.
#Disclaimer
The sample scripts are not supported under any Microsoft standard support program or service. The sample scripts are provided AS IS without warranty of any kind. Microsoft further disclaims all implied warranties including, without limitation, any implied warranties of merchantability or of fitness for a particular purpose. The entire risk arising out of the use or performance of the sample scripts and documentation remains with you. In no event shall Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the scripts be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary loss) arising out of the use of or inability to use the sample scripts or documentation, even if Microsoft has been advised of the possibility of such damages.#
Now on to the good stuff. PowerShell makes it easy to get information about certificates. Using get-childitem and selecting one certificate we can see all the information available
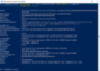
While you can collect all of this information we are going to limit this down to just the Thumbprint, Subject, Issuer, NotBefore, NotAfter, and FriendlyName. We are also going to add a custom value of ExpiresinDays and ScriptLastRan. Next, we use a PowerShell script to collect the information and publish it to a custom wmi class.
mrbodean/AskPFE
Next create a configuration item that uses the script to publish the certificates in the local machine personal store, the local machine trusted publishers, and the local machine trusted root certificate stores to wmi that will allow the hardware inventory to collect the information.
The documentation for using configuration items is available at:
Configuration items for client-managed devices - Configuration Manager
https://docs.microsoft.com/en-us/sccm/compliance/deploy-use/create-configuration-baselines
https://docs.microsoft.com/en-us/sccm/compliance/deploy-use/deploy-configuration-baselines
https://docs.microsoft.com/en-us/sccm/compliance/deploy-use/monitor-compliance-settings
These steps will extend the Hardware Inventory to collect the certificate information that has been published in WMI. To extend the inventory you must use a MOF file, MOF files are a convenient way to change WMI settings and to transfer WMI objects between computers. For more info see Using MOF Files
Once the configuration item runs and publishes the data info WMI, the next time hardware inventory runs for systems in the test collection the certificate information will be available for reporting in Configuration Manager.
These steps will create console query that you can use to search for systems with a specific certificate thumbprint
This is a SQL query that can be used to view the certificate inventory data and can also be used as the basis for creating a custom report
Select sys.Name0 as ‘Name’, Location0 as ‘Certificate Location’, FriendlyName0 as ‘Friendly Name’, ExpiresinDays0 as ‘Expires in Days’, Issuer0 as Issuer, NotAfter0 as ‘Not After’, NotBefore0 as
‘Not Before’, Subject0 as Subject, Thumbprint0 as Thumbprint, ScriptLastRan0 as ‘Script last Ran’
from v_GS_CM_CERTINFO
Inner Join v_R_System as sys ON v_GS_CM_CERTINFO.ResourceID = sys.ResourceID
Thank you for reading, and I hope this helps you out!
Continue reading...
#Disclaimer
The sample scripts are not supported under any Microsoft standard support program or service. The sample scripts are provided AS IS without warranty of any kind. Microsoft further disclaims all implied warranties including, without limitation, any implied warranties of merchantability or of fitness for a particular purpose. The entire risk arising out of the use or performance of the sample scripts and documentation remains with you. In no event shall Microsoft, its authors, or anyone else involved in the creation, production, or delivery of the scripts be liable for any damages whatsoever (including, without limitation, damages for loss of business profits, business interruption, loss of business information, or other pecuniary loss) arising out of the use of or inability to use the sample scripts or documentation, even if Microsoft has been advised of the possibility of such damages.#
Now on to the good stuff. PowerShell makes it easy to get information about certificates. Using get-childitem and selecting one certificate we can see all the information available

While you can collect all of this information we are going to limit this down to just the Thumbprint, Subject, Issuer, NotBefore, NotAfter, and FriendlyName. We are also going to add a custom value of ExpiresinDays and ScriptLastRan. Next, we use a PowerShell script to collect the information and publish it to a custom wmi class.
mrbodean/AskPFE
Next create a configuration item that uses the script to publish the certificates in the local machine personal store, the local machine trusted publishers, and the local machine trusted root certificate stores to wmi that will allow the hardware inventory to collect the information.
- Download https://github.com/mrbodean/AskPFE/... Inventory/Inventory Machine Certificates.cab to c:tempExamples
- Navigate to Assets and ComplianceOverviewCompliance SettingsConfiguration Baselines
- Click on “Import Configuration Data” (You will find this as a button on the top toolbar or in the context menu when you right click on Configuration Baselines
- Select C:tempExamplesInventory Machine Certificates.cab
- Click Yes on the warning “The publisher of Inventory Machine Certificates.cab file could not be verified. Are you sure that you want to import this file?”
- Click next twice to progress through the wizard and once complete, click close.
- You will now see a new sub folder named Custom under Configuration Items (Assets and ComplianceOverviewCompliance SettingsConfiguration ItemsCustom) and a configuration item named “Inventory Machine Certificates” in the Custom folder.
- You will also see a Configuration baseline named “Inventory Machine Certificates”
- Deploy this baseline to a test collection
The documentation for using configuration items is available at:
Configuration items for client-managed devices - Configuration Manager
https://docs.microsoft.com/en-us/sccm/compliance/deploy-use/create-configuration-baselines
https://docs.microsoft.com/en-us/sccm/compliance/deploy-use/deploy-configuration-baselines
https://docs.microsoft.com/en-us/sccm/compliance/deploy-use/monitor-compliance-settings
These steps will extend the Hardware Inventory to collect the certificate information that has been published in WMI. To extend the inventory you must use a MOF file, MOF files are a convenient way to change WMI settings and to transfer WMI objects between computers. For more info see Using MOF Files
- Download https://raw.githubusercontent.com/m.../ConfigMgr Certificate Inventory/CertInfo.mof to c:tempExamples
- Create a new Custom Device Client Setting (AdministrationOverviewClient Settings)
- Name the setting “Custom HW Inventory” and only enable Hardware Inventory
- Select Hardware Inventory on the left just under General
- Ensure Enable hardware inventory on clients is set to yes
- The default schedule is for 7 days, update the schedule if you would like to change it
- Click the “Set Classes …” button
- Click on the “Import …” button
- Select the c:tempExamplesCertInfo.mof
- Once back on the Hardware Inventory Classes dialog ensure the CertInfo (cm_CertInfo) class is enabled
- Click Ok
- Click on the “Import …” button
- Click Ok (again)
- Deploy the “Custom HW Inventory” Client Setting to a test collection.
Once the configuration item runs and publishes the data info WMI, the next time hardware inventory runs for systems in the test collection the certificate information will be available for reporting in Configuration Manager.
These steps will create console query that you can use to search for systems with a specific certificate thumbprint
- Download https://raw.githubusercontent.com/m...Mgr Certificate Inventory/Find_Cert_Query.MOF to c:tempExamples
- Navigate to MonitoringOverviewQueries
- Click on “Import Objects”, this is available a button on the top toolbar and the context menu when you right click on Queries
- Click next to navigate through the wizard
- On the MOF File Name step, select c:tempExamplesFind_Cert_Query.MOF
- Once the import completes, you will see a query named “Find Machines with a Certificate by thumbprint”

- Once you have systems reporting the certificates as part of the inventory you can run this report
- When you run this report, it will prompt you for the thumbprint of a certificate to search for
- If any systems are found with the certificate the system name and the thumbprint will be returned by the query
This is a SQL query that can be used to view the certificate inventory data and can also be used as the basis for creating a custom report
Select sys.Name0 as ‘Name’, Location0 as ‘Certificate Location’, FriendlyName0 as ‘Friendly Name’, ExpiresinDays0 as ‘Expires in Days’, Issuer0 as Issuer, NotAfter0 as ‘Not After’, NotBefore0 as
‘Not Before’, Subject0 as Subject, Thumbprint0 as Thumbprint, ScriptLastRan0 as ‘Script last Ran’
from v_GS_CM_CERTINFO
Inner Join v_R_System as sys ON v_GS_CM_CERTINFO.ResourceID = sys.ResourceID
Thank you for reading, and I hope this helps you out!
Continue reading...