Server Man
Well-Known Member
- May 17, 2015

- Android

- Chrome Mobile 70.0.3538.80
Azure Advanced Threat Protection (Azure ATP) provides invaluable insights on identity configurations and suggested security best-practices across the enterprise. A key component of Azure ATP’s insights is Lateral Movement Paths or LMPs. Azure ATP LMPs are visual guides that help you quickly understand and identify exactly how attackers can move laterally inside your network. The purpose of lateral movements within a cyber-attack kill chain are for attackers to gain and compromise your sensitive accounts towards domain dominance. Azure ATP LMPs provide easy to interpret, direct visual guidance on your most vulnerable sensitive accounts, assists in helping you mitigate and close access for potential attacker domain dominance.
Lateral movement attacks, using non-sensitive accounts to gain access to sensitive accounts, can be accomplished through many different techniques. The most popular methods used by attackers are credential theft and Pass the Ticket. In both methods, your non-sensitive accounts are used by attackers for lateral moves by exploiting machines that share stored log-in credentials in accounts, groups and machines with your sensitive accounts.
Where can I find Azure ATP LMPs?
Every computer or user profile discovered by Azure ATP has a Lateral movement paths tab.
The LMP tab provides different information depending on sensitivity of the entity:
When you click the tab, Azure ATP displays the most recently discovered LMP. Each potential LMP is saved for 48 hours following discovery. You can view older LMPs by clicking on view a different date.
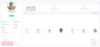
V2.56 of Azure ATP adds two additional LMP capabilities. Discover when potential LMPs were identified and where.
When
From the Activities tab, we’ve added an indication when a new potential LMP were identified:
Where
LMP can now directly assists with your investigation process. Azure ATP security alert evidence lists provide the related entities that are involved in each potential lateral movement path. The evidence lists directly help your security response team increase or reduce the importance of the security alert and/or investigation of the related entities. For example, when a Pass the Ticket alert is issued, the source computer, compromised user and destination computer the stolen ticket was used from, are all part of the potential lateral movement path leading to a sensitive user.
The existence of the detected LMP makes investigating the alert and watching the suspected user even more important to prevent your adversary from additional lateral moves. Trackable evidence is provided in LMPs to make it easier and faster for you to prevent attackers from moving forward in your network.
It’s never too late
Security insights are never too late to prevent the next attack and remediate damage. For this reason, investigating an attack during the domain dominance phase provides a different, but important example. Typically, while investigating a security alert such as Remote Code Execution, if the alert is a true positive, your domain controller may already be compromised. But where did the attacker gain privileges, and what was their path into your network? How can the attack be remediated? These are critical questions to answer in order to remediate the attack, recover and prevent the next one.
Assuming your network architecture is standard, the compromised user running remote commands on the domain controller must be a sensitive user. As a sensitive user, Azure ATP has mapped and identified their potential LMPs. In a case where this user account is already compromised and succeeded at running commands on a domain controller, LMP is a fast, effective method to understanding. How did the attacker gain user credentials? How did they achieve lateral moves in your network towards domain dominance? Although LMPs are only potential methods, combining LMPs with security alerts can provide invaluable insights into how attackers were able to use lateral moves within your organization to achieve their goals and the steps you need to take to prevent them in the future.
Additional data formats
LMP data is also available in the Lateral Movement Paths to Sensitive Accounts report. This report lists the sensitive accounts that are exposed via lateral movement paths and includes paths that were selected manually for a specific time period or included in the time period for scheduled reports. Customize the included date range using the calendar selection.
Learn more about investigations using lateral movement paths.
Get Started Today
Leveraging the scale and intelligence of the Microsoft Intelligence Security Graph, Azure ATP is part of Microsoft 365’s Enterprise Mobility + Security E5 suite.
Continue reading...
Lateral movement attacks, using non-sensitive accounts to gain access to sensitive accounts, can be accomplished through many different techniques. The most popular methods used by attackers are credential theft and Pass the Ticket. In both methods, your non-sensitive accounts are used by attackers for lateral moves by exploiting machines that share stored log-in credentials in accounts, groups and machines with your sensitive accounts.
Where can I find Azure ATP LMPs?
Every computer or user profile discovered by Azure ATP has a Lateral movement paths tab.
The LMP tab provides different information depending on sensitivity of the entity:
- Sensitive users – potential LMP(s) leading to this user are shown.
- Non-sensitive users and computers – potential LMP(s) the entity is related to are shown.
When you click the tab, Azure ATP displays the most recently discovered LMP. Each potential LMP is saved for 48 hours following discovery. You can view older LMPs by clicking on view a different date.
V2.56 of Azure ATP adds two additional LMP capabilities. Discover when potential LMPs were identified and where.
When
From the Activities tab, we’ve added an indication when a new potential LMP were identified:
- Non-sensitive users and computers – when this entity was identified in a potential LMP leading to a sensitive user
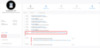
Where
LMP can now directly assists with your investigation process. Azure ATP security alert evidence lists provide the related entities that are involved in each potential lateral movement path. The evidence lists directly help your security response team increase or reduce the importance of the security alert and/or investigation of the related entities. For example, when a Pass the Ticket alert is issued, the source computer, compromised user and destination computer the stolen ticket was used from, are all part of the potential lateral movement path leading to a sensitive user.
The existence of the detected LMP makes investigating the alert and watching the suspected user even more important to prevent your adversary from additional lateral moves. Trackable evidence is provided in LMPs to make it easier and faster for you to prevent attackers from moving forward in your network.
It’s never too late
Security insights are never too late to prevent the next attack and remediate damage. For this reason, investigating an attack during the domain dominance phase provides a different, but important example. Typically, while investigating a security alert such as Remote Code Execution, if the alert is a true positive, your domain controller may already be compromised. But where did the attacker gain privileges, and what was their path into your network? How can the attack be remediated? These are critical questions to answer in order to remediate the attack, recover and prevent the next one.
Assuming your network architecture is standard, the compromised user running remote commands on the domain controller must be a sensitive user. As a sensitive user, Azure ATP has mapped and identified their potential LMPs. In a case where this user account is already compromised and succeeded at running commands on a domain controller, LMP is a fast, effective method to understanding. How did the attacker gain user credentials? How did they achieve lateral moves in your network towards domain dominance? Although LMPs are only potential methods, combining LMPs with security alerts can provide invaluable insights into how attackers were able to use lateral moves within your organization to achieve their goals and the steps you need to take to prevent them in the future.
Additional data formats
LMP data is also available in the Lateral Movement Paths to Sensitive Accounts report. This report lists the sensitive accounts that are exposed via lateral movement paths and includes paths that were selected manually for a specific time period or included in the time period for scheduled reports. Customize the included date range using the calendar selection.
Learn more about investigations using lateral movement paths.
Get Started Today
Leveraging the scale and intelligence of the Microsoft Intelligence Security Graph, Azure ATP is part of Microsoft 365’s Enterprise Mobility + Security E5 suite.
- Learn more about Azure ATP here: Technical Documentation
- Start a trial from our Azure Advanced Threat Protection Product Page
- Join the Azure ATP community: Technical Community
Continue reading...