Server Man
Well-Known Member
- May 17, 2015

- Windows 10

- Chrome 77.0.3865.120
Can your Identity Security Posture be fixed?
A fact known to security teams worldwide is that most cyber-attacks leverage existing unpatched vulnerabilities (ever heard of BlueKeep?), and have taught us that often the most effective proactive security strategy for any organization is maintaining healthy security posture. If you haven’t done it already, patch your operating system while you read this!
As attacks continue to grow, in both sophistication and scale, maintaining a strong identity security posture has never been more important. Malicious actors and attackers are constantly searching for exploitable weak spots. According to a recent survey by Code42, unpredictable humans remain the weakest link in data security.
What can be done to mitigate the risks that users may unknowingly create?
Identity security posture
Proactive management and improvement of your identity security posture is the best defensive strategy against unpredictable human behavior.
By investigating network traffic and gathering data directly from your identity infrastructure (Active Directory schema and domain controllers as well as other services) Azure Advanced Threat Protection (Azure ATP) can identify common misconfigurations and weak spots that can be used to compromise your environment.
By providing you with the relevant information to remediate the risks and assure they don’t resurface, our latest Identity Security Posture Assessment capabilities are your best new line of defense.

Azure ATP is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
Azure ATP also enables SecOps analysts and security professionals struggling to detect advanced attacks in hybrid environments to:
Take immediate action to secure your organization
Using Azure ATP’s identity security posture assessments, a Security Administrator can quickly understand if an assessment requires their immediate attention using the suggested remediation. By providing data, context (most critical entities) and urgency ranking, your security administrators can refocus on what really matters.
Ready to dive even deeper? Azure ATP provides the relevant information on why each assessment is important to your organization, along with all the contextual information needed for your security team to act and improve your security posture.
Field example: Still hunting legacy protocol usage? The hunt is over.
The security community needs an easy way to identify and access use of legacy authentication protocols such as NTLMv1 in organizations of all sizes. Additionally, most organizations accept the risk of legacy protocols because they fear existing line of business apps will cease functioning.
Leveraging Azure ATP sensors on the domain controller, we surface the riskiest entities in your organization that continue authenticating with NTLMv1 as a remediation guide. It’s key to remediate legacy protocols before disabling NTLMv1 usage completely with use of a LAN Manager authentication level group policy.
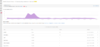
Field example: Stop unconstrained Kerberos delegations in their tracks
Several methods of Active Directory-based attacks are known to leverage often misconfigured entities, especially ones set with unconstrained Kerberos delegation.
Entities capable of unconstrained Kerberos delegation enjoy nearly unlimited organizational power, allowing them to impersonate any service as another entity, much like how domain controllers operate in Active Directory. It is strongly recommended to modify this permission to allow for more controlled, constrained, or resource-based Kerberos delegation.
By querying the active schema, Azure ATP surfaces all non-domain controller entities currently configured in your organization with unconstrained Kerberos delegation, enabling you to act immediately to remediate the threat.
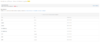
Demonstrate impact
Improving your identity security posture as an ongoing process is a proven way to make your organization more resilient to threats.
Together, with our team of security researchers and developers, these new Azure ATP assessments provide continuous support to your security admins and CISOs by providing an accurate picture of what your security posture looks like and which issues require immediate remediation.
Use Azure ATP to provide your teams with all the context they need to monitor, improve, and secure your environment and deliver better, long-term security across your enterprise.
Azure ATP is already a part of Microsoft Secure Score and we will add dedicated scoring for each of these new assessments to Secure Score’s identity category in a later update.
Sign-up to attend our webinar where we walk you through how to leverage Azure ATP to maximize your security posture.
Learn more:
If you’re one of the many enterprise customers already using Azure ATP and want to use these new Identity Security Posture Management assessments, turn on the new identity threat investigation experience today.
Just starting your Azure ATP journey? begin a trial of Microsoft Threat Protection to experience the benefits of the most comprehensive, integrated, and secure threat protection solution for the modern workplace.
Join the Azure ATP community for the latest updates and news about identity security posture assessments and management.
Continue reading...
A fact known to security teams worldwide is that most cyber-attacks leverage existing unpatched vulnerabilities (ever heard of BlueKeep?), and have taught us that often the most effective proactive security strategy for any organization is maintaining healthy security posture. If you haven’t done it already, patch your operating system while you read this!
As attacks continue to grow, in both sophistication and scale, maintaining a strong identity security posture has never been more important. Malicious actors and attackers are constantly searching for exploitable weak spots. According to a recent survey by Code42, unpredictable humans remain the weakest link in data security.
What can be done to mitigate the risks that users may unknowingly create?
Identity security posture
Proactive management and improvement of your identity security posture is the best defensive strategy against unpredictable human behavior.
By investigating network traffic and gathering data directly from your identity infrastructure (Active Directory schema and domain controllers as well as other services) Azure Advanced Threat Protection (Azure ATP) can identify common misconfigurations and weak spots that can be used to compromise your environment.
By providing you with the relevant information to remediate the risks and assure they don’t resurface, our latest Identity Security Posture Assessment capabilities are your best new line of defense.
Azure ATP is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization.
Azure ATP also enables SecOps analysts and security professionals struggling to detect advanced attacks in hybrid environments to:
- Monitor users, entity behavior, and activities with learning-based analytics
- Protect user identities and credentials stored in Active Directory
- Identify and investigate suspicious user activities and advanced attacks throughout the kill chain
- Provide clear incident information on a simple timeline for fast triage
Take immediate action to secure your organization
Using Azure ATP’s identity security posture assessments, a Security Administrator can quickly understand if an assessment requires their immediate attention using the suggested remediation. By providing data, context (most critical entities) and urgency ranking, your security administrators can refocus on what really matters.
Ready to dive even deeper? Azure ATP provides the relevant information on why each assessment is important to your organization, along with all the contextual information needed for your security team to act and improve your security posture.
Field example: Still hunting legacy protocol usage? The hunt is over.
The security community needs an easy way to identify and access use of legacy authentication protocols such as NTLMv1 in organizations of all sizes. Additionally, most organizations accept the risk of legacy protocols because they fear existing line of business apps will cease functioning.
Leveraging Azure ATP sensors on the domain controller, we surface the riskiest entities in your organization that continue authenticating with NTLMv1 as a remediation guide. It’s key to remediate legacy protocols before disabling NTLMv1 usage completely with use of a LAN Manager authentication level group policy.
Field example: Stop unconstrained Kerberos delegations in their tracks
Several methods of Active Directory-based attacks are known to leverage often misconfigured entities, especially ones set with unconstrained Kerberos delegation.
Entities capable of unconstrained Kerberos delegation enjoy nearly unlimited organizational power, allowing them to impersonate any service as another entity, much like how domain controllers operate in Active Directory. It is strongly recommended to modify this permission to allow for more controlled, constrained, or resource-based Kerberos delegation.
By querying the active schema, Azure ATP surfaces all non-domain controller entities currently configured in your organization with unconstrained Kerberos delegation, enabling you to act immediately to remediate the threat.
Demonstrate impact
Improving your identity security posture as an ongoing process is a proven way to make your organization more resilient to threats.
Together, with our team of security researchers and developers, these new Azure ATP assessments provide continuous support to your security admins and CISOs by providing an accurate picture of what your security posture looks like and which issues require immediate remediation.
Use Azure ATP to provide your teams with all the context they need to monitor, improve, and secure your environment and deliver better, long-term security across your enterprise.
Azure ATP is already a part of Microsoft Secure Score and we will add dedicated scoring for each of these new assessments to Secure Score’s identity category in a later update.
Sign-up to attend our webinar where we walk you through how to leverage Azure ATP to maximize your security posture.
Learn more:
- Understanding Identity Security Posture
- Security assessment: Entities exposing credentials in cleartext
- Security assessment: Legacy protocols usage
- Security assessment: Weak cipher usage
- Security assessment: Unsecure Kerberos delegation
- Security assessment: Domain Controllers with Print Spooler service available
- Security assessment: Dormant entities in sensitive groups
If you’re one of the many enterprise customers already using Azure ATP and want to use these new Identity Security Posture Management assessments, turn on the new identity threat investigation experience today.
Just starting your Azure ATP journey? begin a trial of Microsoft Threat Protection to experience the benefits of the most comprehensive, integrated, and secure threat protection solution for the modern workplace.
Join the Azure ATP community for the latest updates and news about identity security posture assessments and management.
Continue reading...