R
RAJU.MSC.MATHEMATICS
On 23-06-2020 , Recently Some cybersecurity researchers found WASTEDLOCKER ransomware attacked to organization computers.
The way of attack is explained by the below article
https://blog.fox-it.com/2020/06/23/wastedlocker-a-new-ransomware-variant-developed-by-the-evil-corp-group/
After reading the above article, I took the following precautions
step 01
I added the following links in the hosts file, which is located in C:\windows\system32\drivers\etc\
## Begining Block WASTEDLOCKER ransomware address added on 24-06-2020
#
0.0.0.0 adsmarketart.com
0.0.0.0 advancedanalysis.be
0.0.0.0 advertstv.com
0.0.0.0 amazingdonutco.com
0.0.0.0 cofeedback.com
0.0.0.0 consultane.com
0.0.0.0 dns.proactiveads.be
0.0.0.0 mwebsoft.com
0.0.0.0 rostraffic.com
0.0.0.0 traffichi.com
0.0.0.0 typiconsult.com
0.0.0.0 websitelistbuilder.com
0.0.0.0 bettyware.xyz
0.0.0.0 celebratering.xyz
0.0.0.0 fakeframes.xyz
0.0.0.0 gadgetops.xyz
0.0.0.0 hotphonecall.xyz
0.0.0.0 justbesarnia.xyz
0.0.0.0 kordelservers.xyz
0.0.0.0 tritravlife.xyz
0.0.0.0 veisllc.xyz
0.0.0.0 wineguroo.xyz
0.0.0.0 devicelease.xyz
0.0.0.0 guiapocos.xyz
0.0.0.0 ludwoodgroup.xyz
0.0.0.0 respondcritique.xyz
0.0.0.0 triomigratio.xyz
0.0.0.0 uplandcaraudio.xyz
0.0.0.0 woofwoofacademy.xyz
0.0.0.0 advokat-hodonin.info
0.0.0.0 penaz.info
0.0.0.0 paiolets.com
0.0.0.0 flablenitev.site
0.0.0.0 lendojekam.xyz
0.0.0.0 lgrarcosbann.club
0.0.0.0 lpequdeliren.fun
0.0.0.0 transvil2.xyz
0.0.0.0 szn.services
0.0.0.0 utenti.info
0.0.0.0 utenti.live
# end Block WASTEDLOCKER ransomeware address ===============
step 02
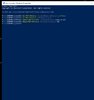
also, i executed the following commands by using PowerShell.exe with admin rights
Set-MpPreference -DisableBehaviorMonitoring $false
Set-MpPreference -MAPSReporting 2
Remove-MpPreference -ExclusionProcess rundll32.exe
Remove-MpPreference -ExclusionExtension dll
step 03
i blocked program "rundll32.exe" in windows firewall under this location C:\Windows\system32\ for both inbound , outbound connection with any IP addresses with any protocols.
Sources is taken from:
WastedLocker: A New Ransomware Variant Developed By The Evil Corp Group
I say thanks to the author of the article from this forum, for the detailed explanations of the ransomeware.
Thanks for reading my post, If you like this post means, then share this post to other users and give upvotes

Continue reading...
The way of attack is explained by the below article
https://blog.fox-it.com/2020/06/23/wastedlocker-a-new-ransomware-variant-developed-by-the-evil-corp-group/
After reading the above article, I took the following precautions
step 01
I added the following links in the hosts file, which is located in C:\windows\system32\drivers\etc\
## Begining Block WASTEDLOCKER ransomware address added on 24-06-2020
#
0.0.0.0 adsmarketart.com
0.0.0.0 advancedanalysis.be
0.0.0.0 advertstv.com
0.0.0.0 amazingdonutco.com
0.0.0.0 cofeedback.com
0.0.0.0 consultane.com
0.0.0.0 dns.proactiveads.be
0.0.0.0 mwebsoft.com
0.0.0.0 rostraffic.com
0.0.0.0 traffichi.com
0.0.0.0 typiconsult.com
0.0.0.0 websitelistbuilder.com
0.0.0.0 bettyware.xyz
0.0.0.0 celebratering.xyz
0.0.0.0 fakeframes.xyz
0.0.0.0 gadgetops.xyz
0.0.0.0 hotphonecall.xyz
0.0.0.0 justbesarnia.xyz
0.0.0.0 kordelservers.xyz
0.0.0.0 tritravlife.xyz
0.0.0.0 veisllc.xyz
0.0.0.0 wineguroo.xyz
0.0.0.0 devicelease.xyz
0.0.0.0 guiapocos.xyz
0.0.0.0 ludwoodgroup.xyz
0.0.0.0 respondcritique.xyz
0.0.0.0 triomigratio.xyz
0.0.0.0 uplandcaraudio.xyz
0.0.0.0 woofwoofacademy.xyz
0.0.0.0 advokat-hodonin.info
0.0.0.0 penaz.info
0.0.0.0 paiolets.com
0.0.0.0 flablenitev.site
0.0.0.0 lendojekam.xyz
0.0.0.0 lgrarcosbann.club
0.0.0.0 lpequdeliren.fun
0.0.0.0 transvil2.xyz
0.0.0.0 szn.services
0.0.0.0 utenti.info
0.0.0.0 utenti.live
# end Block WASTEDLOCKER ransomeware address ===============
step 02
also, i executed the following commands by using PowerShell.exe with admin rights
Set-MpPreference -DisableBehaviorMonitoring $false
Set-MpPreference -MAPSReporting 2
Remove-MpPreference -ExclusionProcess rundll32.exe
Remove-MpPreference -ExclusionExtension dll
step 03
i blocked program "rundll32.exe" in windows firewall under this location C:\Windows\system32\ for both inbound , outbound connection with any IP addresses with any protocols.
Sources is taken from:
WastedLocker: A New Ransomware Variant Developed By The Evil Corp Group
I say thanks to the author of the article from this forum, for the detailed explanations of the ransomeware.
Thanks for reading my post, If you like this post means, then share this post to other users and give upvotes


Continue reading...